We all know that security of information is important, more so when the information concerns banking and financial services, military and defence networks, and various government offices spread all over the globe. The challenge would increase with the introduction of quantum computers that are expected sooner than later. So, let’s find out what’s being done.
Modern communication technologies and data security are heavily dependent on encryptions to maintain the secrecy of the information being transmitted or stored. In any cryptographic algorithm, information security depends entirely on the privacy of keys. Today’s state-of-the-art public key infrastructure (PKI), which is mostly used across the globe to secure the internet, is based on mathematically complex algorithms. The security is based on the assumption that it is virtually impossible, even for the most advanced classical computer, to perform certain mathematical functions, like prime factorisation of a very large integer, in a reasonable time.
However, with the rapid advancements in quantum computing and quantum algorithms, this assumption does not hold very strong. Google’s claim of quantum supremacy in October 2019, to perform a sequence of operations in 200 seconds that would take a classical supercomputer about thousands of years to complete, points toward the vulnerability of the existing cryptographic systems in front of an adversary having access to a quantum computer. Quantum key distribution (QKD) is a method of key exchange that eliminates any probability of eavesdropping. Fundamental rules of quantum mechanics ensure that any case of eavesdropping changes the system irreversibly, and the attempts of eavesdropping get detected.
Basics of cryptography
Cryptography is commonly used in communication networks to protect the data being transmitted from the hands of malicious or unwanted users. Before transmission, the information (plain text message) is encrypted to form a ciphertext that is unreadable without access to the corresponding decrypting key. At the receiver, the ciphertext is decrypted to get back the original plain text message. The process is depicted in Fig. 1.
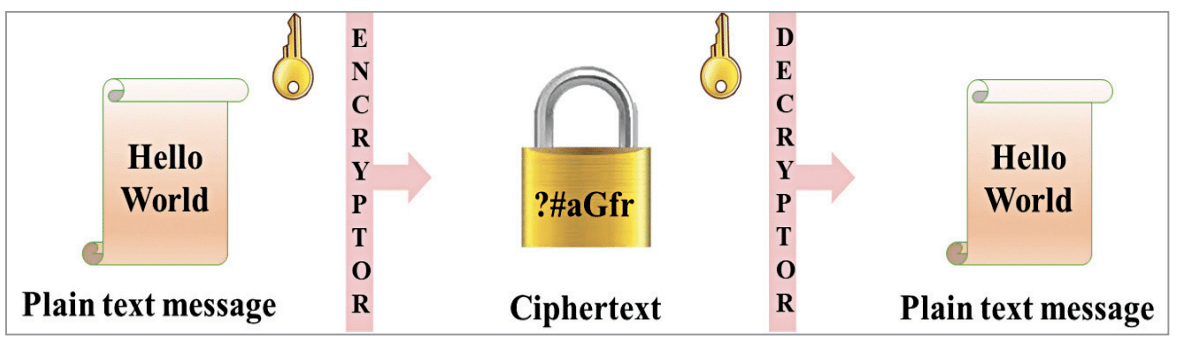
Depending on the key used during the encryption and decryption processes, the cryptographic algorithms can be broadly classified into two categories:
Symmetric key cryptography:
In this case, the same key is used for encryption as well as decryption. The key lengths are relatively smaller (128-256 bits). Examples: Advanced Encryption System (AES), Data Encryption Standard (DES).
Asymmetric/Public key cryptography:
In this case, the keys used for the encryption and decryption process are different. A public key is used for encryption and a mathematically related private key is used for decryption. Data encrypted with a public key can only be decrypted with the corresponding private key. Also, it is impossible to derive the private key from the public key. Key lengths for asymmetric key cryptography are relatively longer (>2048 bits). Examples: RSA, DSA, ECC, Diffie-Hellman algorithm.
Challenges with present cryptography
The existing cryptographic algorithms suffer from several shortcomings, such as:
- Intrusions in the system remain undetectable. There have been instances of huge financial and reputational loss when intrusions got unidentified for a long time.
- The security is based on the assumption that certain mathematical operations are impossible to be performed in considerable time, even by the most sophisticated classical computer. But security will be compromised with the advent of quantum computers.
- Brute force attacks on keys are also increasing due to the low frequency of key updates.
- Asymmetric encryption is 2-3 times slower than symmetric encryption due to longer key lengths and the complexity of the encryption algorithms used in asymmetric encryption. As one of the keys is public, both longer key lengths and complex algorithms are prerequisites.
Given the above facts, should we be worried? The answer is, yes. The report of IBM Security titled ‘Cost of a Data Breach Report 2020’ states the average total cost of a data breach is $3.86 million, having an approximately 10% increase since 2014. In 2015, Michele Mosca presented a detailed overview of cybersecurity in the threat of possible advancements in quantum computing. He came up with an equation, popularly known as Mosca’s inequality:
D+T ≥QC
where D stands for the amount of time we need to keep our data secure, T the time it will take our systems to transition from classical to post-quantum, and QC the time it will take quantum processors to reach a scale where they can breach existing encryption protocols. There has been a consensus among experts that this inequality has already been breached in the year 2017.
QKD and its architecture
Quantum mechanics, formulated around 100 years back, is now maturing to an extent that its practical applications in the area of computing, communications, sensors, devices, etc have the potential to revolutionise these with unprecedented advances having far-reaching implications. QKD is one of the most emerging applications of quantum communications and will see a plethora of uses and deployments in the years to come.
QKD is a key sharing mechanism implemented in quantum cryptography to generate a perfectly random key that is shared between two nodes (traditionally called Alice and Bob). It is based on the principles of quantum mechanics, that is, Heisenberg’s uncertainty principle and no-cloning principle, to guarantee secure key distribution. These principles enable Alice and Bob to generate a shared random secure key that is known only to them. This secure key is used to encrypt the messages that need to be sent by Alice and to extract the original messages from received signals by Bob (and vice-versa). An important and unique feature of QKD is that both Alice and Bob can detect the presence of a third party trying to learn about the key, which inherently makes the generated keys highly secure from eavesdropping.
The sharing of keys between Alice and Bob takes place securely employing a quantum channel and an authenticated classical channel. The quantum channel for this system is typically either single-mode fibre or free space, whereas the classical channel can be a transmission over the internet. Quantum channel and classical channel together form a QKD link. The architecture of a point-to-point (P2P) QKD link is shown in Fig. 2.
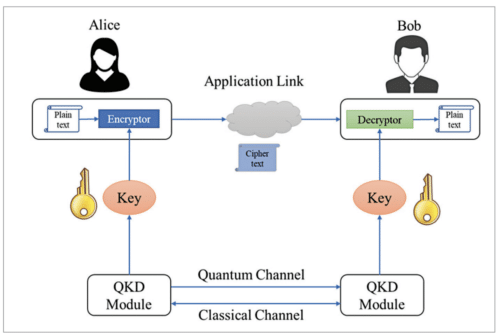
The generation of shared secret keys through QKD involves several steps as follows:
- Alice (application sender) and Bob (application receiver) are connected through a classical channel that is pre-authenticated. It can be any IP/Ethernet link.
- Alice sends the quantum information, called qubits, over the quantum channel. Depending upon the QKD protocol used Alice can use the quantum properties of light, such as polarisation, phase, or timeof-arrival.
- Bob performs quantum measurements on the received qubits as per the QKD protocol used. There are always some losses in the quantum channel.
- Alice and Bob share some information over the classical channel to arrive at a common secret key. Eavesdropping on the classical channel does not affect the secrecy of the key.
- The raw key undergoes a sifting process in which Alice and Bob discard incompatible qubits based on the protocol used.
- Alice and Bob check the quantum bit error rate (QBER) to check for eavesdropping (by an adversary, commonly called Eve) on the quantum channel. If QBER is less than a defined threshold, the key is further processed. Otherwise, the communication is aborted.
- Due to imperfections in the source, detector, and transmission media, the sifted keys may have some errors that are corrected using error correction algorithms.
- Finally, the keys undergo a privacy amplification process. The keys are compressed by suitable factors to conceal any information that may have gone to Eve during the key generation process.
- The generated keys are stored along with key-ID and delivered to the application on request.
- Keys generated in the QKD system can be mathematically proved to be secure and it is not based on any assumption
QKD protocols
Charles Bennett and Gilles Brassard proposed the first quantum cryptography protocol in 1984 at a conference in Bangalore (now Bengaluru). This protocol is popularly known as BB84. After that several QKD protocols have been proposed and proved to be information-theoretically secure. The evolution of various QKD protocols was influenced by the following factors:
- Ease of implementation on a physical system
- Rate of secret key generation
- Supported distance between Alice and Bob
- Immunity from quantum hacking activities that exploit the imperfections in QKD devices
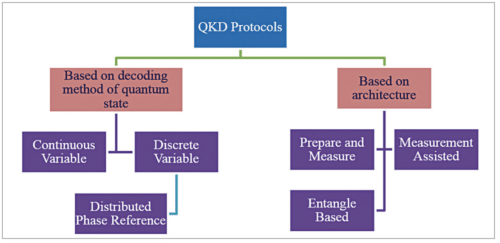
Based on the decoding method of quantum states, QKD protocols can be broadly divided into two categories:
Continuous variable (CV) QKD:
Here information is encoded using the position and momentum quadrature of a quantised electromagnetic field in an infinite-dimensional Hilbert space.
Discrete variable (DV) QKD:
DV-QKD protocols encode information with discrete variables of finite dimension, such as phase, polarisation, or time bin of single photons.
A special type of DV-QKD protocol uses the time and phase of weak coherent pulses to prepare qubits, and coherence between consecutive pulses are checked to identify eavesdropping. This is called distributed phase reference (DPR) protocol. Differential phase shift (DPS) and coherent one-way (COW) are examples of DPR protocols. They are widely used due to the long range and high rate of key generation. On the other side, based on the architecture of protocols, QKD protocols can be grouped into three categories:
Prepare and measure (P&M):
A transmitter (Alice) prepares and sends a quantum state to a receiver (Bob) that measures it to arrive at the final shared key. Example: BB84 protocol.
Measurement assisted:
Two transmitters prepare and send quantum states to a receiver (traditionally called Charlie) that performs a joint measurement. The final key is shared between two transmitters. Here both Alice and Bob act as transmitters. Examples: Measurement DeviceIndependent (MDI) and Twin-Field (TF) QKD protocols.
Entangle based:
A transmitter (Charlie) prepares a bipartite entangled quantum state and sends its two parts to two receivers that measure the quantum state. The final key is shared between two receivers. Here both Alice and Bob act as receivers. Example: E91 QKD protocol.
Standardisation activities
Different standard development organisations—like the European Telecommunication Standards Institute (ETSI), the International Telecommunication Union (ITU), and the International Standards Organization (ISO)—are developing standards for QKD. This will eventually allow multivendor interoperability and open new development opportunities. ITU has come up with a series of standards for the QKD network. Also, a few standards are under preparation. The ITU-T standards in force are:
- Y.3800: Overview on networks supporting quantum key distribution
- Y.3801: Functional requirements for quantum key distribution networks
- Y.3802: Quantum key distribution networks—Functional architecture
- Y.3803: Quantum key distribution networks—Key management
- Y.3804: Quantum key distribution networks—Control and management
Application
There has been a substantial increase in the internet population along with the number of devices per capita and average data usage. With the rollout of 5G networks, a much greater number of devices are expected to be connected to the internet. Data security will be more challenging and crucial than ever. As per the report from The Insight Partners titled ‘Quantum Cryptography Market To 2027,’ the Global QKD market is expected to touch $2 billion by 2027 with a CAGR of 39.2%.
The induction of QKD systems in existing networks to make them quantum secure does not require the entire network to be redesigned. The existing infrastructure can be upgraded with quantum security. The government of India in its Budget 2020 announced a National Mission on Quantum Technologies & Applications (NM-QTA) with a total budget outlay of ₹ 8,000 crore ($1.2 billion approx.) for five years to be implemented by the Department of Science & Technology (DST).
QKD systems have their relevance in all the networks that carry confidential, sensitive, financially important, or strategic data. Leakage of this data to a malicious user can cause financial, reputational, or strategic loss. The potential users are:
- Banking, financial services, and insurance (BFSI) sectors
- Networks encompassing government offices located across the country
- Healthcare and pharmaceutical industries
- Military and defense networks
- Telecommunications and the IT industry
Contribution of C-DOT in QKD
C-DOT is a premier telecom R&D institute under the Department of Telecommunications, government of India. C-DOT has the legacy of delivering cutting-edge indigenous technology, hardware, and software solutions that are especially targeted to meet the requirements of the rural areas that were digitally unserved for a long time. In the field of QKD, C-DOT has achieved the following milestones:
- Indigenously developed complete hardware and software for both Alice and Bob nodes using both DPS and COW QKD protocols
- Achieved a secure key rate of greater than 1kbps over 100km fibre with a quantum bit error rate (QBER) of 5%
- Successfully simulated photon number splitting (PNS) attack
- Filed two patents with Indian Patent Office:
- Device and Method of Synchronisation in Quantum Key Distribution (QKD) System
- An Efficient Method to Automatically Align Phase Modulator with Pulse Generator/Intensity Modulator in the Alice Node of DPSQKD System
- Integrated the QKD system with C-DOT router as well as postquantum cryptography (PQC) system as per ETSI standard
Arka Mukherjee works as Senior Research Engineer at Centre for Development of Telematics (C-DOT), telecom R&D centre of the government of India. He has more than nine years of experience in embedded systems design for optical access networks




