ECC is computed by point multiplication on elliptic curves over prime integer fields or binary polynomial fields. The implementation of ECC on WSNs is primarily interested in prime integer fields since binary polynomial field mathematics is poorly supported by the slow processors. Operations of ECC scale linearly. This gives ECC an advantage over RSA on processors with small word sizes. Also, ECC grows in advantage as the key size grows.
Random key predistribution scheme. Basically, the scheme consists of three phases: key pre-distribution, shared-key discovery and path-key establishment.
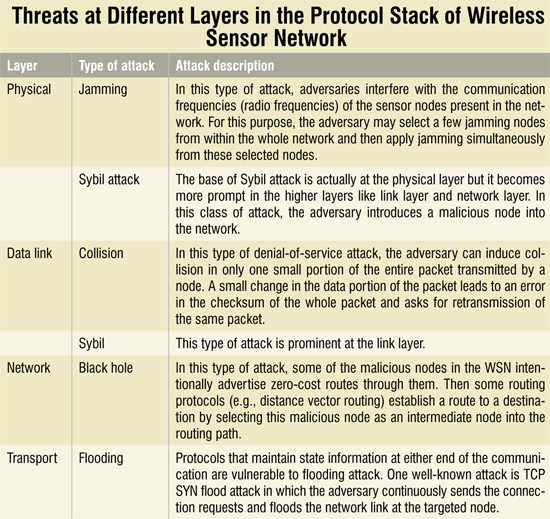
In the key pre-distribution phase, each sensor node randomly selects ‘m’ distinct cryptographic keys from a large key pool ‘S,’ and stores them in its memory. This set of ‘m’ keys is called the node’s key ring. The number of keys in the key pool, ‘S,’ is chosen such that two random subsets of size ‘m’ in ‘S’ share at least one key with some probability ‘p.’
After the nodes are deployed, a key setup phase is performed. During this phase, each pair of neighbouring nodes attempts to find a common key that the nodes share. If such a key exists, the key is used to secure the communication link between these two nodes.
After key-setup is complete, a connected graph of secure links is formed. Nodes can then set up path keys with their neighbours with whom they do not share keys. If the graph is connected, a path can always be found from a source node to any of its neighbours. The source node can then generate a path key and send it securely via the path to the target node.
The size of key pool ‘S’ is critical to both the connectivity and the resilience of the scheme. Connectivity is defined as the probability that any two neighbouring nodes share one key. Resilience is defined as the fraction of the secure links that are compromised after a certain number of nodes are captured by the adversaries.
Way forward
Key management system’s purpose is to secure communication in wireless sensor networks without producing much overhead. More schemes should be developed to make efficient use of sensor nodes’ limited resources. Greater emphasis should be given to the security in key management schemes, particularly as a majority of sensor node deployment is in hostile environments.
The authors are from Department of Computer Science & Engineering, National Institute of Tech-nology, Hamirpur (HP)










