Hari Om Prakash
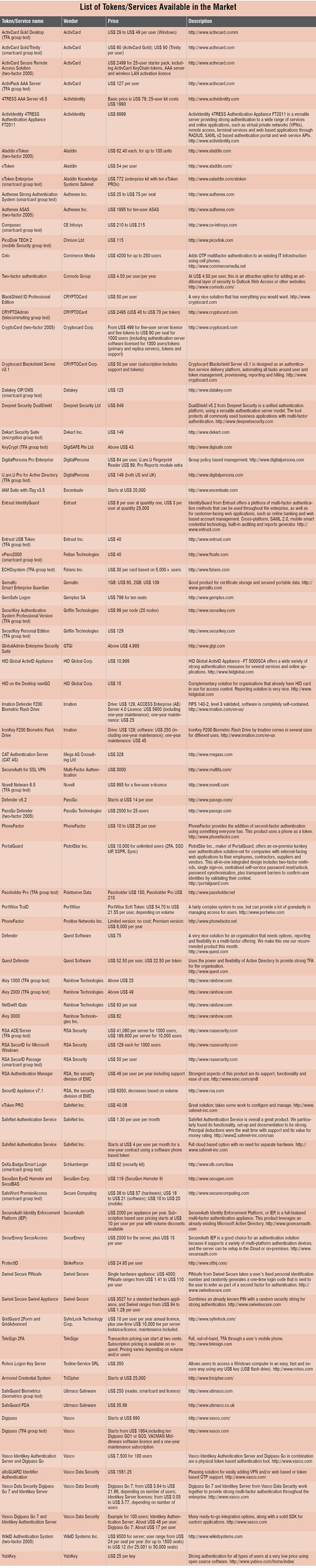
By now, we know what two-factor authentication (TFA) is and how it can be an extremely useful security tool. In this concluding part of the article, we will discuss the advantages and disadvantages of TFA, along with various tokens/services available in the market for activating TFA.
Advantages of two-factor authentication
1. TFA could drastically reduce the incidence of online identify theft, phishing expeditions and other online frauds, because the victim’s password would no longer be enough to give a thief access to his or her personal information.
2. In a simple way, using TFA increases the level of security. The higher the security, the lower the incidence of fraud. The lower the incidence of fraud, the higher the confidence to transact online.
Disadvantages of two-factor authentication
1. Increasing the level of security increases inconvenience to the user. Users have to activate TFA and they have to use mobile phones or other devices for authentication. They cannot access their accounts if they are not carrying such devices during authentication (like, in some companies, users are not allowed to use mobile phones or biometric devices). It is observed that a large proportion of users do not opt for the higher level of security.

2. To hack TFA, bad guys must acquire either the physical component of the login, or must gain access to the cookies or tokens placed on the device by the authentication mechanism. This can happen in several ways, including phishing attacks, malware or credit-card-reader skimming. However, there is another way: account recovery. RSA SecurID hardware token has already been hacked. So, such type of attacks may result in turning off TFA.
3. TFA solution relies on the use of physical hardware devices or tokens to get the dynamic one-time password (OTP). Here are two factors of overhead. First, the user has to carry hardware tokens every time while authenticating with services. Second, introducing tokens for such authentication systems will increase the cost, such as the cost to acquire tokens and pay to get services, like SMSes. Some services have now started to charge money for sending SMSes to users. Hardware tokens (like RSA SecurID) contain a battery, so every time a battery dies, the token must be replaced, which results in a cost to replace it. Again, in the event of a token being damaged or lost, this will also require provisioning of a new token to the user.
Surveys indicate that an organisation with 600 users would typically expect up to ten tokens lost per month, equating to 1.67 per cent of the install base. If the hardware token costs US$ 50 and it costs an additional US$ 50 to dispatch the token, then the cost of handling lost tokens alone can add a cost of US$ 1000 per month, which should also be factored-in to any solution costs.
Conclusion
Passwords are not secure enough, and if someone gets your password, the person can easily access your account and can do anything with your account, like deleting data or sharing sensitive data with public. To prevent hackers, you have to create a complex password by using some alpha and non-alpha characters, including special characters. The main problem of using such type of techniques is the difficulty in remembering such complex passwords. As per surveys, it is difficult for human beings to remember new complex passwords for multiple accounts.
By using TFA, it becomes more difficult for hackers to take over your account by impersonating you. TFA technique provides an extra, second layer of security to your traditional authentication system. Your account can only be accessed after successful authentication of both layers of security.
With the introduction of TFA and required physical tokens with this service, such technology introduces advantages to improve the level of security and disadvantages to increase the cost. Now, futuristic industries are looking for token-less authentication solutions that can provide compelling cost-saving and lower the complexity and on-going cost, because of the ease of using token form factor and the ease with which the solution can be provisioned and used.
Concluded
The Author is working as a scientist/engineer (SD) at Systems Engineering Group, ADRIN, Department of Space, and is involved in developing applications in the field of network security and secure programming language design and implementation field










