As industrial IoT (IIoT) integration surges, so do security concerns. Let’s delve into the rising threat landscape and the role of the security model in fortifying IIoT defences and safeguarding critical infrastructure.
Industrial IoT (IIoT) security has gained tremendous importance in recent years. With the rise of IIoT and the increasing integration of operational technologies (OT) with the internet, the need for robust security measures has become paramount. Industrial IoT, often referred to as OT, has transformed industries across the board. The advent of 5G technology has made OT assets integral to the manufacturing, healthcare, and robotics sectors. These technologies have improved operational efficiency and enhanced worker safety by reducing accidents in industrial settings.
In the past, OT systems operated in isolation; however, they are interconnected today, leading to more efficient and complex systems. Remote operations have also become increasingly common, highlighting the need for secure IIoT infrastructure. While IIoT offers numerous benefits, it also introduces security challenges. Connecting OT systems to the internet inherently involves some level of risk. Recent news reports have highlighted industrial cyberattacks, such as the Ukrainian electric grid attack and the Saudi oil refinery attack, showcasing the vulnerabilities of increased connectivity.
Ransomware attacks, in particular, have emerged as a significant threat to the manufacturing sector. In 2021 alone, there were ten successful ransomware attacks targeting manufacturing companies. The consequences of such attacks are severe, disrupting production, encrypting data, and causing financial losses.
Challenges In India
India is not immune to these threats. Recent attacks on organisations like Oil India, Dr Reddy’s Laboratories, and Tata Power have underscored the critical nature of IIoT security. The healthcare sector has not been spared, with institutions like AIIMS falling victim to ransomware attacks, paralysing essential services. One of the most concerning trends is the rise of state-sponsored cyberattacks. Countries like China and others are known to engage in targeted campaigns, launching attacks on critical infrastructure worldwide. These attacks have been a constant threat, with significant incidents reported yearly.
The connectivity dilemma with the expansion of IIoT has exposed security gaps. This is depicted in Fig. 1.
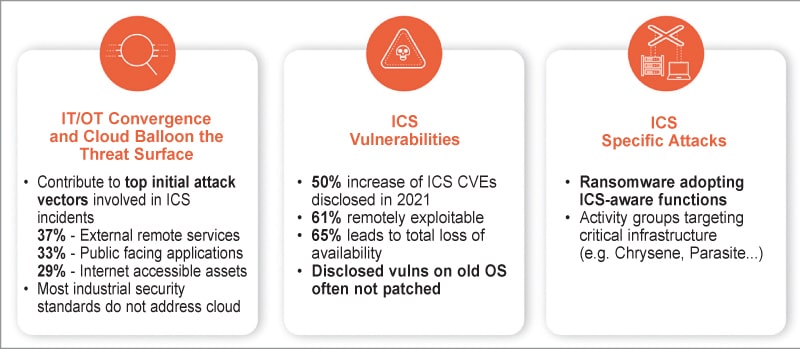
Many OT systems are externally accessible, with public-facing applications and internet accessibility, making them susceptible to attacks. Vulnerabilities in industrial control systems (ICS) have increased by 50%, with 61% being remotely exploitable. The loss of availability, a critical element in the CIA triad (confidentiality, integrity, and availability), is a major concern, with 65% of attacks leading to downtime. Outdated operating systems like Windows XP and Windows 7 pose additional risks. Many organisations still use these unsupported systems, making them easy targets for exploitation. Furthermore, ransomware attacks targeting specific industries have become a significant menace.

As we continue to embrace the potential of Industrial IoT, it is crucial to address the security challenges that come with it. The convergence of OT and IT systems demands a comprehensive approach to cybersecurity. Organisations must prioritise securing their IIoT infrastructure to protect against potential threats and ensure the uninterrupted operation of critical systems. In this era of connectivity, security is not an option but a necessity. With vigilance, education, and robust cybersecurity measures, we can safeguard our industrial IoT assets and pave the way for a more secure and prosperous future. As organisations worldwide embrace the opportunities presented by digital transformation, they must also be acutely aware of the risks that come hand in hand.
| Notable industrial cyberattacks and the growing threat landscape in IIoT |
| In the world of Industrial IoT (IIoT), the potential for catastrophic cyberattacks cannot be underestimated. Here are some examples that highlight the devastating consequences of such attacks: • The Ukraine power grid attack. Initiated by a spear-phishing email targeting a high-profile individual, this attack compromised both IT and OT systems, culminating in a network takeover. In just six hours, 230,000 people faced a devastating power grid shutdown amid freezing temperatures. • Saudi oil refinery attacks. Targeted critical infrastructure in oil and gas, nuclear, and manufacturing sectors, posing a grave threat to national security and international stability. • Norsk hydro ransomware attacks. Causing disruptions in aluminium production across approximately 170 plants, these attacks led to significant financial losses, highlighting the vulnerability of critical industrial infrastructure to cyber threats. • Colonial pipeline hack. Resulting in widespread fuel and gasoline shortages, this cyberattack disrupted the crucial energy supply chain, leading to fuel shortages at gas stations, and underscoring the vulnerability of critical infrastructure to cyber threats, thereby raising concerns about national security and resilience. However, new attacks are emerging every day. A 2021 report indicated 10 successful ransomware attacks on the manufacturing segment. The potential loss is staggering, considering the encryption of data and shutdown of machines. As the IIoT landscape expands, so does the threat landscape. The lessons learned should serve as a clarion call for heightened vigilance, rigorous training, and stringent security protocols to protect against future cyber onslaughts. |
The changing face of threats







