Critical IoT | Converging Technologies | Cloud-Connected Enterprises
8 Critical IoT Security Technologies
A recent report by Gartner predicts that there will be 20.4 billion connected Internet of Things (IoT) devices by 2020,...
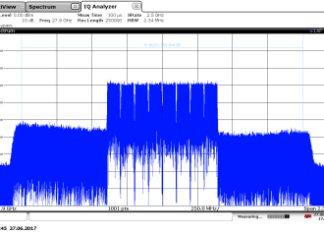
The First Signal & Spectrum Analyser to Offer 2 GHz Internal...
Developers of 5G radio access technologies, high-end radar systems and automotive applications need a very large bandwidth to analyze wideband signals. A new hardware...
Camouflaged Past, Omnipresent Future
Automation is defined as carrying out a set of predefined procedures to achieve a specific outcome. Introduction of engineering automation can be dated back...
Build Secure IoT | Border Security | Stricter Government
Building the IoT Security Village
People are often portrayed as the weakest link in a security chain. People can be fooled into revealing passwords, or...
Basic Electronics Guide
A basic guide for students and hobbyists to learn basic electronics through practical presentable circuits.
Upon completion of this slideshow you will be able to...
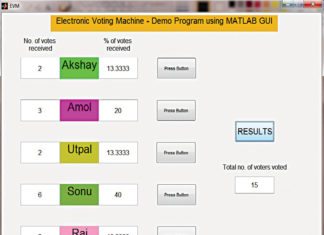
Electronic voting machine demo using MATLAB GUI
Electronic voting machines (EVMs) are used to conduct elections in India. These machines provide straightforward and effortless features to voters to cast their votes...
Energy From Mountains | Advanced Adiabatic Compressed Air Energy Storage
In this video, the presenter is going to give you a detailed information of a new type of renewable energy called Advanced Adiabatic Compressed Air Energy...
Tutorial: Simple LED Desk Lamp
Whether for work or leisure, we usually end up spending hours together on a computer. A desk lamp helps enhance efficiency, output, and comfort...
Hybrid Power and Signal Connector Saves Cost And Space
IP67-rated SuperCon Series connector combines power and data transmission to save cost and space in interface wiring applications.
GARNER N.C., August 10, 2017 -- CONEC...
Multilayered Approach | Security Appliance | Smart Thermostat
Locking Down the IoT
Security and risk (S&R) professionals are under increasing pressure to secure IoT deployments to minimize the risk of data breaches, disruptive...