The buzz in the web market is two-factor authentication (also known as TFA, 2FA, two-step verification, multi-factor authentication). Many users hold multiple accounts on multiple websites, and most of them use the same password for multiple accounts. If their password is hacked on one website, their accounts on other websites get vulnerable too. Passwords are not secure enough—if someone gets your password, they can easily access your account and can do anything with your account like deleting your data, sharing your sensitive data with the public, hijacking, etc.
By using two-factor authentication, it becomes more difficult for hackers to impersonate you and take over your account. With an increase in cyber attacks or exploitation of the first level, there is need for a second level of authentication that adds more security to services or contents like e-mail, bank accounts, social accounts, etc.
What is two-factor authentication
Authentication is concerned with assuring an authentic communication. Till now, you may be aware of one-factor authentication only, where you are asked for a user login name and password (for example: Gmail login in Fig. 1 and SBI online net banking login in Fig. 2).

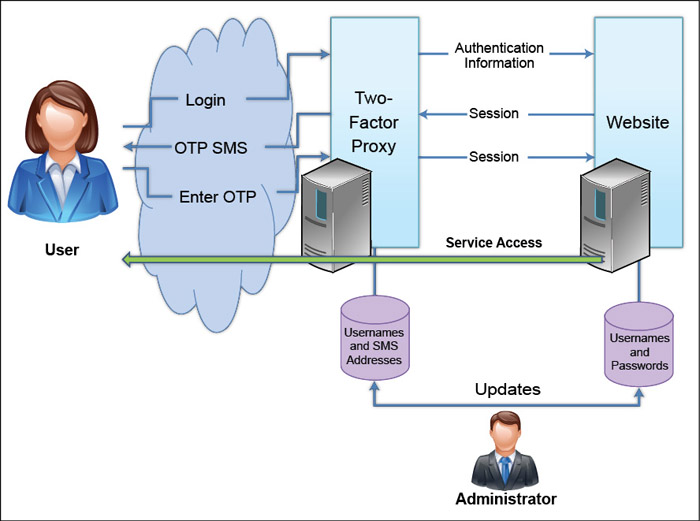
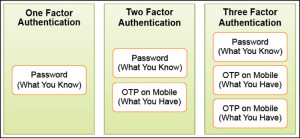
Two-factor authentication provides an extra second layer of security with your traditional authentication system. Your account can be accessed only after successful authentication of both layers of security. Fig. 4 shows an architectural view of TFA. Two-factor authentication adds a second level of authentication—‘something you have’ like a phone OTP SMS (Fig. 3)—to the first level of authentication which is ‘something you know’ like an account login and password.
In an account login system, you have to enter the user ID and password. You can give out your user ID to anyone, but the password has to be kept a secret. In TFA system, after you enter your login details, you will get a second password or code sent to your registered mobile phone number or e-mail address, which is known as a one-time password (OTP). There might be a third level of authentication, or a replacement of second level, where you have to be physically present during authentication. This type of authentication technique is known as ‘something you are’—like a biometric finger scanning, eye scanning or a voice print.


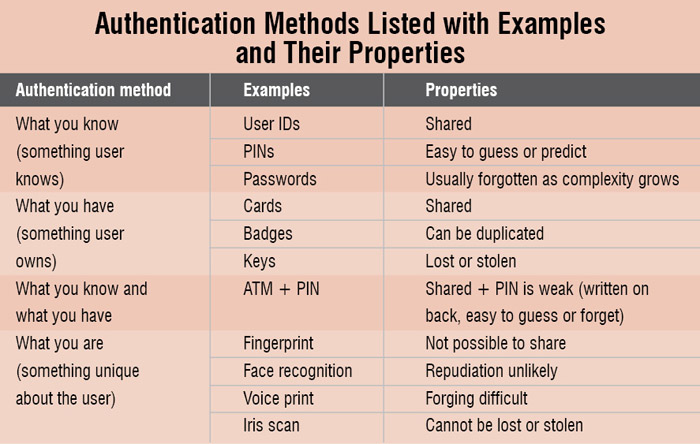
TFA requires a user to provide two out of three types of credentials before being able to access an account. The three types of authentication techniques (as shown in Fig. 5) are:
1. What you know—something
a user knows like a password or PIN.
2. What you have—something a user owns like an ATM card or mobile phone.
3. What you are—something unique about a user like fingerprint or voice print.
What you know
Sometimes called the first level of authentication, this simple approach includes authentication of personal identification number (PIN) or password. To prevent hacking, you have to create a complex password by using some alpha and non-alpha characters including special characters. One problem you might face when using this authentication technique is that you have to remember even complex passwords, while the next authentication techniques do not need any memory power. This kind of technique is commonly known as knowledge-factor authentication, where a user has to prove the knowledge of a secret in order to authenticate.
Some examples of ‘what you know’ are:
Password. A password is a secret word or string of characters used for user authentication. This is the most commonly used mechanism for authentication. Many TFA techniques rely on password as one factor of authentication.
PIN. A PIN is a secret numeric password, typically used in ATMs.
Pattern. A pattern is a sequence of cells in an array used for authenticating users, such as pattern-based authentication used in Android devices (Fig. 6).
What you have

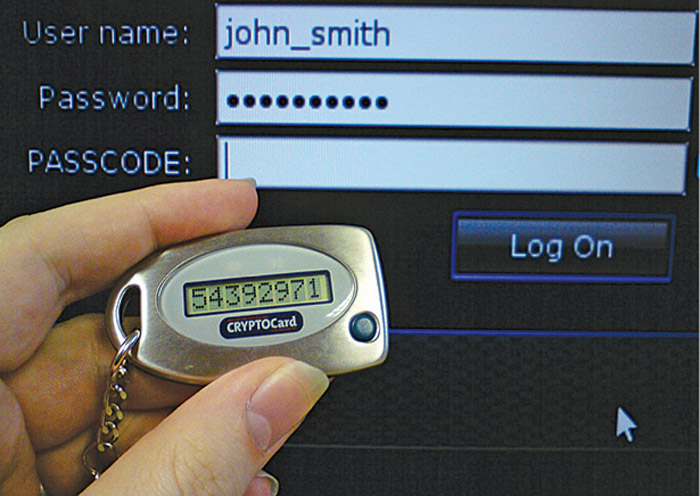
A user has to use what he or she has for authentication, such as an ATM card, mobile phone, e-token, etc. During authentication, websites or services will send a temporary password, OTP, to your registered mobile phone number. Some e-token devices (like connected tokens, where they are required to connect with the system) are just like pen drive dongles used to connect with the system. An e-token uses a digital signature or some kind of a secret key during authentication only. It is very difficult to use those keys outside the application. Other e-token devices (like disconnected tokens in Fig. 8, where they are not required to connect with the system) have a digital display (SecurID token in Fig. 7) to show you the unique key every time you need to authenticate with the website. This factor is very prone to attacks. Keys can easily be stolen; if lost, a thief can use such keys to open the lock. So, it has become mandatory to use additional authentication or a secure way of storing the keys.