Just as in the paper world you cannot stop anyone from seeing the address on the letters’ envelope, the same is true for an e-mail. If someone alters that address, it does not go to the right place, and if someone alters the return address, the recipient may not know where it has come from, or it may not, if delivery fails, be returned to the correct sender.
We are familiar with the paper world and it has some benefits. You can usually see if someone has already opened your mail. The post office can often cope with wrong addressing and still get it to the right place. E-mail is rather different. There is no way of telling who reads the mail unless you take actual steps to make it impossible. The e-mail post office cannot cope with any address errors whatsoever. It has no idea if any of the addresses on the mail are correct and cannot tell if they have been altered. There is no plain envelope to stop people reading the contents and it is possible for hackers, government agencies and almost anyone else to read the mail. Proof of delivery is worth the paper it is printed on.
Most people send mail in two ways—with a web-based interface like Yahoo!, Gmail or Hotmail, or with an e-mail client program like Outlook or Eudora. When we send a message with an e-mail program on our personal computer (or cell phone or PDA), we have to specify a server so that our e-mail program knows where to send the message. This server is like our local post office. An e-mail program talks directly to the server using the computer protocol (language) known as SMTP. This is like dropping off a letter at the local post office.
When we use some tool on our personal computer for an Internet connection to communicate with a Web server, the language that the Internet connection uses is HTTP—hypertext transfer protocol. When we send our message with Web mail, the Web server contacts its SMTP server and sends our message to it.
To summarise, when we use the Web-based e-mail programs like Gmail (which is also a cloud service), the Web server already has the SMTP/POP3/IMAP3 address inserted. If we want to access other e-mail accounts maintained by any other e-mail server (term used for SMTP/POP3/IMAP3 server), it can be done using these Web-based services, by mentioning the specific e-mail server address. Let us see the security in both these cases.
In case of e-mail clients like Outlook or any other non-Web-based application, we can apply security on the message and send the e-mail. This kind of security is shown in Fig. 2. In case of Web-based scenario, we can have an SSL kind of environment between client and Web server, and SSL or some other kind of security between the Web server and the e-mail server. Between Web server and client, we can invoke SSL in the form of https://www.site.com. Here SSL, which runs at the transport layer (default port 443), takes care of all the communication being encrypted between client and Web server. Between Web server and e-mail server, we can have SSL-enabled SMTP in the form SMTPS, SSL-enabled POP3 in the form POP3S, SSL-enabled IMAP in the form IMAP3S or some other kind of security. It all depends upon the requirement and ease of usage. The above-mentioned scenarios are depicted in Fig. 2.
We have mentioned a phrase, ‘some other kind of security’ many a times above, but what does it mean? In the scenario of Web-based e-mail access, we can take S/MIME or MOSS as different security standards that can be used. Similarly, in the scenario of non-Web-based access, we can take PGP or PEM as different security standards. But MOSS and PEM are not much used these days for e-mail security.
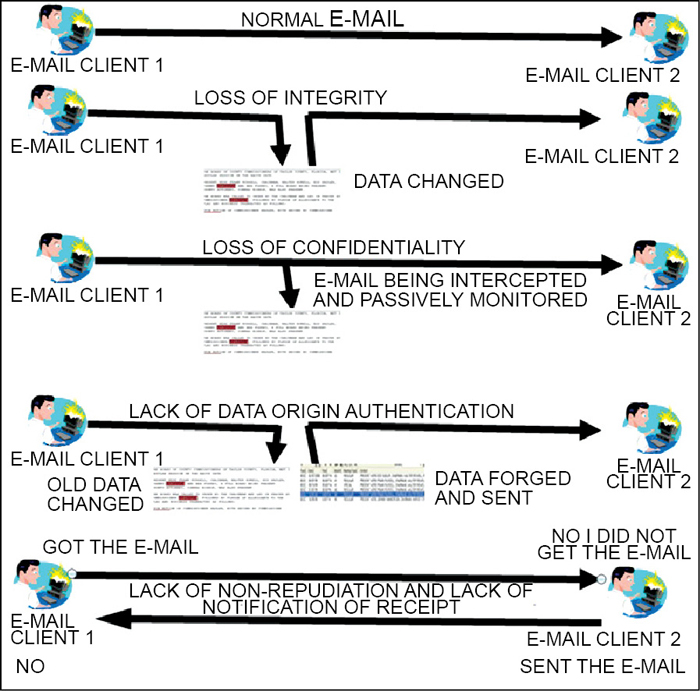
Issues in e-mail security
E-mail can be made secure, but we have to take a few things into account. The first thing to understand is that we cannot do much about the addresses, or the subject line. Nothing about these can be made secure. Different systems may allow us to secure the message text of the e-mail, but we have to be very certain what that security is, when it is added, when it is removed and how we could prove it had been secured, afterwards. These are fundamental and important if we are going to rely on the security mechanisms later as proof that something happened.