E-mail security has been a growing concern over the past few years. The average individual, who uses e-mail, naively believes that his e-mail is private and secure but he is wrong, as the electronic world is filled with snoopers who can access all types of data over the network. As the world goes digital, with more and more raw information about individuals available electronically, the need for security increases. Ubiquity and speed of e-mail have made it increasingly effective. So providing reliance over this medium has become an inevitable requirement.
The e-mails of today can be made secure by encrypting the content on an external medium and sending this as an attachment over the mail. But this increases the size of the mail and makes it inconvenient for the user. There are other systems that provide specific security and are strongly tied to the mail servers and browsers. Enter the answer—secure e-mail (Se-mail). Run it just like an ordinary mail but click on the secure button and you are done. Somehow it seems obvious to anyone that the immense complexity of the computer can be made safe and secure by a single act (the laying on of hands perhaps).
Let us take an analogy that explains a typical e-mail scenario. Suppose a person is in a crowded room and spots a friend to whom he wants to convey an important message, but he does not want to yell. He writes a message on a paper-slip and asks the person next to him to pass it on, trusting no one will read it on its journey through dozens of hands—hands belonging to people he has never met. What are the odds that the person’s friend will be the only one to read the message intended for him or her alone? Untold number of people, including you and me, employ this useful aspect of network and Internet communication to exchange data and documents.

Whilst there are strong legal penalties that deter snooping in the traditional media, such as posted or courier mail, the sheer novelty of computer-aided communication has created gaps in the legal net, allowing for tampering and snooping on others’ e-mails or personal information. As the world goes digital, with more and more raw information about individuals available electronically, the need for security increases.
The major problems that ordinary e-mails suffer are data origin authentication and connectionless integrity apart from privacy. Which means that it is quite difficult with the ordinary e-mail to prove that the sender actually wrote the message, or that it has not been tampered with? Here, we will be discussing about the various challenges in e-mail security and try to find out the solution for the same. At the same time, we will discuss a few tips and tricks that can ensure e-mail security.
How e-mail works
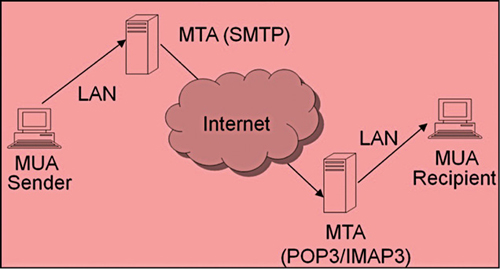
Sending an e-mail message is like sending an ordinary letter (not a courier, registered letter or speed post). When you send a letter, you drop it off at your local post office. Your local post office looks at the address and figures out which regional post office the letter should go to. Then the regional post office looks at the address and finds out which local post office is closest to your recipient. Finally, the recipient’s local post office delivers your letter to its recipient.
Computers are like post offices, and the simple mail transport protocol (SMTP) is the procedure, rather a protocol which a post office uses to find out where to send the letter next in the process. Any program that sends an e-mail message uses SMTP protocol (default port 25) to deliver that message to the next ‘post office’ for relaying to its final destination.
Now, we have sent the mail using SMTP. What about retrieving the e-mail or reading the e-mail? Well for this, two common protocols are used, which are namely POP3 (post office protocol) (default port 110) and IMAP3 (Internet message access protocol) (default port 143). The working of e-mail is depicted in Fig. 1.
In today’s scenario, the objective for the user might be summarised as follows (borrowing from the paper world): to be certain what they send goes to the right person/place; to be certain that the right person/place can read the information; to be able to use signed receipt as proof to a court or other body; to stop the wrong people from reading personal and private information. Some of these wishes are more difficult than others.