With ineffective cash in hand, market was ripe for widespread popularisation of mobile wallets. For starters, the e-commerce industry observed an increase of about 52 percent transactions taking place through digital payments providing a huge boost to the Digital India campaign. Digital payment usage have gone up by a significant margin recently. Certain mobile wallets are reporting an increase of up to 200 percent in application downloads, with an increase of up to 1500 percent in wallet recharges. The lack of cash influx has resulted in local vendors and hawkers opting mobile wallets. The numbers might seem impressive but would it be correct to assume demonetisation was the sole factor for such popularisation of cashless transactions?
Digital wallet for digital payment
 An argument in favour of mobile wallets is “penetration of cards being very low,” says Umeed Kothavala, CEO and Co-Founder, Extentia Information Technology. And rightly so, we had a plan for getting people to use bank accounts, but we didn’t have the provision of issuing similar number of cards. Add this to the easy availability of smartphones and you have the recipe for a successful wallet that you carry all the time. Smartphones are such an integral part of our lives that we didn’t even realise we were already doing many of our transactions via these pocket wonders. Want to pay your electricity bill, tap and pay. Running low on balance, just one click is all it takes. So, how do they do it?
An argument in favour of mobile wallets is “penetration of cards being very low,” says Umeed Kothavala, CEO and Co-Founder, Extentia Information Technology. And rightly so, we had a plan for getting people to use bank accounts, but we didn’t have the provision of issuing similar number of cards. Add this to the easy availability of smartphones and you have the recipe for a successful wallet that you carry all the time. Smartphones are such an integral part of our lives that we didn’t even realise we were already doing many of our transactions via these pocket wonders. Want to pay your electricity bill, tap and pay. Running low on balance, just one click is all it takes. So, how do they do it?
The numbers look promising as wellMobile wallet segment now covers a very wide range of e-commerce, couponing/cashback, financial inclusion services and daily grocery shopping as well. The areas that are seeing an increase in the recent past are money transfer, mobile recharge, bill payments and utility applications. In Tier-I cities such as Delhi Mumbai, Bengaluru and Chennai the mobile wallets have seen a growth by 110 percent since 2014-15. However, what do you say about rural regions with lesser smartphone coverage? |
A mobile wallet stores digital currency in your name. Online merchants are required to use an API provided by 3rd party payment gateway providers to process transactions. An API is basically a code that merchants can embed on their platforms that allows their website to communicate with the payment gateway provider’s servers as they process their customer’s transactions for them. Paypal, PayUmoney and CCAvenue are the popular ones in the Indian subcontinent for the moment whereas Braintree, a subsidiary of Paypal is also popular outside.
Mobile wallets gaining momentum
Ease of usage has been one of the biggest factors for the success of mobile wallets. Just tap and you are done. Mobile wallets work using third party payment gateways to ensure authentication. The money in a Paytm account can’t be transferred to Freecharge and vice versa, which becomes a problem in some cases when the shopkeeper does not have the same wallet as you. A question in this case comes up is, why not use the same payment gateways to transact between different wallets? Despite this limitation, mobile wallets continue to grow at a rapid rate. A lot more wallets are becoming increasing popular owing to some very lucrative offers. We now have Oxigen wallet, Mobikwik and Citrus pay among others, vying for the top spot.
How does a payment gateway work?Once an order for a transaction is placed, the customer’s web browser encrypts the information to be sent between the browser and the merchant’s server. This can also be done using Secure Socket Layer (SSL) encryption. The payment gateway may allow transaction data to be sent directly from the customer’s browser to the gateway, bypassing the merchant’s systems in certain cases. This reduces the merchant’s Payment Card Industry Data Security Standard (PCI DSS) compliance obligations, without redirecting the customer away from the website. The merchant then forwards the transaction details to their payment gateway. There is another security encrypted layer connection to the payment server hosted by the payment gateway. The information is then forwarded over to the merchant bank, from where it gets redirected to the card issuer who again redirects it to the card issuing bank. Once the transaction is approved or denied depending on the OTP or the pin code, the details are again sent back via the same route. |
USSD is an unappreciated transaction method
For people, unaccustomed to smartphones there are still ways to make a digital payment. Unstructured supplementary service data or USSD, allows you the possibility of checking your bank account via dialling a number over phone itself. This only needs global system for mobile communication (GSM) service on a mobile handset to get the task done. So why is such an ingenious system underrated?
The idea of using only GSM to transact might seem very simple, but the process is a bit odd. And begins with registering your number with your bank. Realistically speaking, banks are a hassle and once you do get it registered, there is a limit of Rs. 5000 per transaction. Also, several forums raise doubts about security of transactions done entirely over GSM. The idea maybe noble, but should be about easing the users not familiar with smartphones. About 7000 USSD transactions amounting to Rs. 73 Lakhs were performed in November 2016 itself. A month later this number grew to 60,000 transactions amounting to Rs. 6.6 crore. State Bank of India (SBI), Industrial Credit and Investment Corporation of India (ICICI), Housing Development and Finance Corporation (HDFC), Punjab National Bank (PNB), Axis Bank and Bank of Baroda (BOB) are the major ones seeing benefit from USSD for the moment.
Banking on InnovationA rather innovative solution for non-smartphone users is being tested out by Yes Bank. The slim sleeve sim card works without any internet access or the need of a smart phone. The wafer-thin sticker can be stuck to any sim card and does not hamper regular mobile performance. The transactions are performed using a patented encrypted SMS technology dedicated to connect with Yes Bank servers. At present the solution is stuck to basic banking services, but the introduction of such a solution opens new areas for exploration. |
Unified payments interface looks to solve problems
Unified Payments Interface (UPI) is a bank-to-bank fund transfer system backed by the Internet and smartphones. Using phone numbers linked to bank accounts, it looks to utilise the immediate payment service (IMPS) to the fullest. “The biggest advantage with UPI is that it is universal and can be easily used between vendors from different banks,” explains Srinivas Dronamraju, Chief Operating Officer, VSoft Technologies. There are already many banks signed up under the scheme offering transaction services via methods as simple as short message service (SMS’s).
How does UPI work?
UPI looks at a digital payment system that consolidates all your payment methods under an always accessible format. Third party API integration can receive payment from an address avoiding the need to share account details or credentials on third party applications or websites. Every digital payment has a source account for debit and a destination account for credit. In UPI architecture, payment addresses are denoted as “account@provider”, which simply stated is an abstract form to represent a handle that uniquely identify the account details. At the end, before the transaction can be completed, these must be resolved to an actual account number/ID.
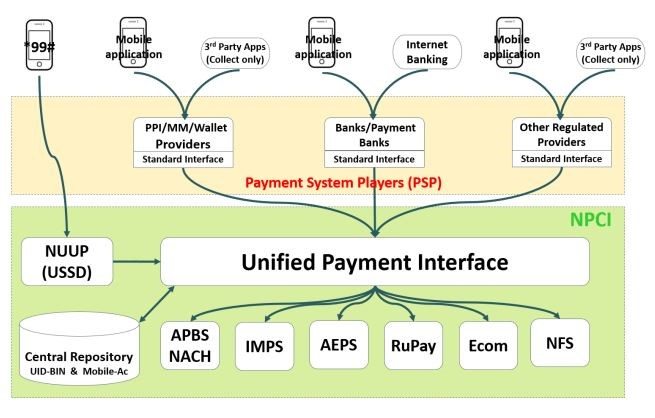
Bharat bill pay system is another approach in this regard. It establishes a unified bill payment system for all needs. Various bill payments take place digitally either via messages or banking applications. Dronamraju says, “Bharat Bill Pay System can be easily used with UPI based systems like the Bharat Interface for Money (BHIM) app.” At present the usage options in the BHIM app however are limited to basic balance check, debit and credit balance. Multiple features are expected to come in with time. This is going to be an option to consider once it becomes free of spam and secures the transactions.
Biometrics for security
Aadhar enabled payment system (AEPS) is another system using government approved identification with improved security. An Aadhar number and a fingerprint is probably one of the toughest passwords you can put on your account. At present the facilities maybe limited to deposit, withdrawals, balance check and Aadhar to Aadhar transfer, but hopefully better systems can come down the line.
The best part is no need of documentation for transactions. Just an Aadhar number linked to a bank account does the trick, and you should probably have your fingers. The Unique Identification Authority of India (UIDAI) matches your fingerprint to your records whereas the bank account matches your Aadhar number to their records. If all goes well, you may very well proceed with the transaction.
| DID YOU KNOW: The RBI classifies every mode of cashless fund transfer or transaction using cards or mobile phones as ‘prepaid payment instrument’. |
Cryptocurrency is enticing
 For people involved in technology heavily can also go for cryptocurrency, but it is a bit complex. The idea of mining currency may sound intriguing, but involves some complex coding besides from the hardware involved. These are gaining momentum over the past decade very heavily, of which the most popular of which being Bitcoin. For layman, mining Bitcoin or Blockchain technology is no less confusing than traversing the labyrinth.
For people involved in technology heavily can also go for cryptocurrency, but it is a bit complex. The idea of mining currency may sound intriguing, but involves some complex coding besides from the hardware involved. These are gaining momentum over the past decade very heavily, of which the most popular of which being Bitcoin. For layman, mining Bitcoin or Blockchain technology is no less confusing than traversing the labyrinth.
Bitcoin is the popular one
Bitcoin mining is one method of cryptocurrency involving Blockchain technology. If you move into a private network, you have a very different Blockchain to consider. Now, mining Bitcoins is a tricky business and has led to actual business for firms operating mine farms. Some mining companies set up cloud farms and sell contracts to the buyer. This might seem shady to some, but the other option is to invest in a hardware. Selecting the right hardware is as challenging a task as they come.
The bitcoin network compensates the miners by releasing bitcoins to contributors based on the computational power they have. But these are 24×7 systems and it makes no sense to do this on your personal laptop. Bitcoins work based on hash power of the system and it calls for having a hash power that can return your investment similarly.
But there’s that dark side
Several users report having a loss after four to five years and eventually selling the hardware as scrap metal with a loss of 21 percent in bitcoins, considering the cost of electricity and the hardware involved. Also, there are concerns if these are singular cases and not the norm considering the cost of mining has increased rapidly. Users have reported a huge rise in Bitcoin mining value over the past couple of years. The price of mining went up by 600$ (380.99$ in October 2015 to 997$ in October 2016) over the course of past one year itself.
How secure are the systems?
 Once something grows this big, woes follow. Human error, phishing attacks and public Wi-Fi are some of the threats faced by the current systems. This does not include more advanced threats like brute force attacks. Dronamraju explains the security in UPI based apps. He says, “Every transaction works based on a virtual address. The account and identity details of the user are always safe.”
Once something grows this big, woes follow. Human error, phishing attacks and public Wi-Fi are some of the threats faced by the current systems. This does not include more advanced threats like brute force attacks. Dronamraju explains the security in UPI based apps. He says, “Every transaction works based on a virtual address. The account and identity details of the user are always safe.”
However, a user of the app recently had to face spam payment requests, causing inconvenience. This raises an issue of the security of the system and bugs in the interface. Other problems inculde freezing of payments page, generating multiple unsuccessful one time passwords (OTPs) or no OTP at all.
The curse of popularisation
“At some point of time, we are going to see the same vulnerability as banks,” says Kothavala. Arguably the biggest concern regarding digital payment is the fact that people are worried about security.
As usage increases, there is a need for improving security in digital wallets transactions. “Digital wallets and mobile wallets have increased usage, adoption and improvised security,” explains Kothavala. However, a study conducted by the Information Systems Audit and Control Association (ISACA) last year says, 47 percent of cybersecurity experts claimed that mobile payments are not secure. The more interesting part of the report was the overwhelming majority of 87 percent anticipated an increase in mobile payment data breaches over the next year.
With the rise in usage there is an increase in security measures including, pattern locks and biometrics. Kothavala adds, “We have to train users as effectively as possible in understanding these methods”. However, taking precautions in case of cyber-attacks is an area that requires attention as well. The level of convenience with digital payments cannot hide the fact that it’s our money in these wallets and we don’t want it going away to any number of unknowns.
Solution for securing transfers
IDComplete from ID Global Solutions Corporation, utilises a secure encrypted irreversible tokenisation process with multi-factor authentication to enable secure real-time cardholder verification. This could be another interesting solution in making digital payments safer. Cryptocurrency like Bitcoin and Blockchain are also some safe steps in this regard. Blockchain is estimated to be able to save global businesses up to $550 billion each year. Per experts it can provide more reliable transparent and authentic way of exchanging assets.
WeChat from Tencent allows some interesting features for securing your mobile wallet. You need to have a separate password for accessing your wallet and a different one for authorising payment. This is different from the phone lock that you might keep. Then there’s the possibility of resetting your password which requires bank details to be re-entered for validation. If this was not enough, big data analytics monitor the transaction data for any suspicious activity and any unauthorised transactions. And if this doesn’t solve things, you can either freeze your account or apply for a cashback. Now that’s a thing or two to learn from.
Lack of inter-wallet transactions
Kothavala explains, “To execute a transaction, the other party should have the capability to accept the payment”. At present, you can execute a transaction only if both parties involved follow the same e-wallet. Which is a major problem. Imagine not being able to use your debit card at a restaurant because the restaurant is registered with a different bank. Interoperability maybe a difficult thing to pull, but if that can happen, this then becomes a whole different ball game. Till then, e-wallets will be gift cards with a wider variety of usage.
Common interface is one of the solutions
Users cannot properly engage in mobile transactions until some common interfaces are defined. A common interface could very well bring out the benefits of using mobile phone as a wallet that allows convenient transactions when compared to earlier channels. Even as a country, we have a unified transaction method of cash to get us around. The lack of a global standard makes the use of digital payment systems more of a hassle than a convenience when traveling abroad.
 Host card emulation (HCE) is one example of securing transactions for mobile devices. It emulates a payment card only a mobile device based on software. It offers multiple benefits to a very wide range of mobile users with near field communication (NFC) payment ecosystem. Earlier, the details were stored on the device calling for a secure element. With the involvement of HCE, this information can now be stored outside the device, hence removing any third-party involvement.
Host card emulation (HCE) is one example of securing transactions for mobile devices. It emulates a payment card only a mobile device based on software. It offers multiple benefits to a very wide range of mobile users with near field communication (NFC) payment ecosystem. Earlier, the details were stored on the device calling for a secure element. With the involvement of HCE, this information can now be stored outside the device, hence removing any third-party involvement.








