
Not a day passes without the news of a major data breach. Although enterprises are spending billions on network defences, they are constantly being subjected to attacks that seem to confound all. According to the 2015 Cyber Threat Defence Report, more than 71% of respondents’ networks were breached and nearly 60% have reported an increase in mobile threats.
Cyber threats are constantly evolving and becoming more sophisticated than ever. The attackers are organized, skilled, and highly motivated. They know that it’s easier to compromise vulnerable endpoints than to directly target servers and databases. On their part, companies too make their vulnerabilities evident when they fall behind in undertaking patching efforts, have inactive host defences, and lack BYOD controls. They find it difficult to secure their weakest links: mobile phones, social media, and laptops and tablets. With most of the users having active social accounts on their mobiles and tablets, attackers indulge in tactics such as spear phishing and water holing to trick unsuspecting users into sharing access credentials or downloading malware-infected files. Once the users have fallen to the ruse, it takes only a moment for hackers to breach the security and exploit other less secure systems.
The Second Coming of a New, Powerful NAC
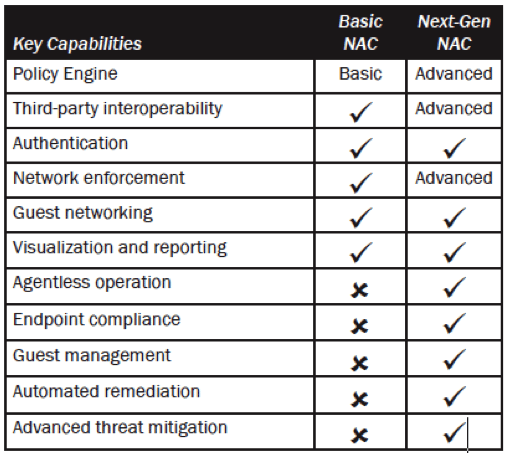
Network access control (NAC) has always been the talk of IT security professionals for well over a decade since it first made its appearance. NAC is a network security solution designed to grant, limit, or deny access to network resources through policies defining acceptable or unacceptable users, devices, and application properties. It provided them with a means to limit access to healthy devices. But device authentication came at a cost: it was cumbersome, costly to implement, and often disrupting users. As organizations begin to tolerate wireless, mobile devices and institute bring-your-own-device (BYOD) polices, the chorus grew for a new, powerful network defense system: the next-gen NAC. The need was very specific: a real-time network visibility, a flexible architecture, limitless policy options, and automated endpoint remediation. Organizations were no longer taking lightly for defense solutions that were limited to managed devices and ‘grant or entry’ network access policies.
There are three primary reasons why many companies are adopting NAC at a furious pace: a complex network infrastructure with inherent control and endpoint visibility gaps; the unfettered practice of BYOD polices; and the need to mitigate advanced threat.
Mitigating Threats with Next-Gen NAC
As attackers are easily able to spot and compromise vulnerable endpoints, it is necessary to prepare the defenses using next generation network access control (NAC) implementations. NAC is particularly effective at addressing security gaps introduced by transient network devices. When a threat is evident, it performs the following functions:
• Alerting you to compliance violations
• Keeping noncompliant, vulnerable endpoints off the network
• Remediating vulnerabilities and security misconfigurations directly or via third-party systems
• Ensuring that host defenses are installed, up-to-date, properly configured, and enabled
When configured optimally, the next-gen NAC will provide you with more endpoint intelligence than you ever dreamt possible. It will give you a bird’s eye-view of the entire network ecosystem in real-time: devices and their types, operating systems, applications, virtual machines, security risks, network locations and a lot more.
Leveraging Next-Gen NAC
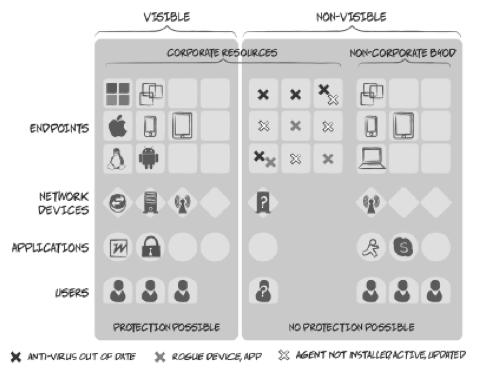
Research studies indicate that companies know approximately 80 percent of what is on their network, and at any given time, as many as 50 percent of those devices have a security or configuration issue. A full-fledged next-gen NAC can see and control—in real time—including visible and nonvisible endpoints, network devices, applications, and users. Well-equipped with passive and active network discovery techniques, today’s next-gen NAC solutions provide unprecedented, real-time network visibility to security professionals. However, a lot of misconceptions about NAC continue to dominate industry professionals, and this is fueled by the restrictions of legacy NAC offerings. At any rate, the next-gen NAC is widely gaining recognition as a core security platform and is poised to help organizations address challenging IT security issues.






