Historically, it has been a challenge to visualise fingerprints on thermal paper, Fear redefines security in every era. Huts began to have doors when people began to worry about their privacy; and forts began to have moats when kings started invading. Banks began to have passwords, homes began to have locks, phones and computers began to have pass-codes, and slowly security became a basic amenity, an all-pervading necessity. As in any field, technology rose to the occasion, and from homes to national borders, high tech began to be deployed at every turn. Still, security and privacy continue to be serious concerns for everybody, albeit of varying degrees.
As always, technologists continue their quest for newer technologies that can protect places, people, and now, their devices and data too. Here, we look at a small sample of the security-related research and experimentation happening across the world. To show how vast an area it is, we shall look at disparate examples that span from data security to public security.
Using the cloud without compromising privacy
In most instances, there is a paradox in using cloud-based services and strong encryption schemes. When you need to perform some operation, say search, on a strongly encrypted database stored on the cloud, but the server cannot decrypt the data, it has no choice but to return all the records to you, letting your computer assume the burden of decrypting and searching the database. So, although your data is secure, the whole point of offloading work to a cloud server is lost in the bargain! On the other hand, if you let the server decrypt the message by sharing the key, security and privacy are compromised.
IBM came out with a solution to this problem, and was granted a patent on it in December 2013. Their ‘fully homomorphic encryption’ offers a way for servers (including cloud ones) to take encrypted data from a user, process it, and send back an encrypted result–all without decrypting the data first! In short, they have solved a mathematical puzzle that has daunted scientists for years–that is, querying of encrypted data without decryption. The first results related to homomorphic encryption were revealed by IBM researcher Craig Gentry in 2009. Although a significant breakthrough, the technique was complex and would take too much time.
As one particular critic pointed out at that time, “Performing a Google search with encrypted keywords—a perfectly reasonably simple application of this algorithm—would increase the amount of computing time by about a trillion.” However, the technique gained new hope in 2013, when two more IBM researchers, Victor Shoup and Shai Halevi, took up Gentry’s original concept and implemented it more practically. They released an open source, GPL-licensed C++ library to perform homomorphic encryption at a low level. They are working on providing higher-level routines.
Other researchers from reputed institutes like the University of Toronto and Massachusetts Institute of Technology are also working on similar techniques, but are all faced with the challenge of making these algorithms faster and more computationally practical.
Non-invasive parcel scanner
How cumbersome it is when the post office or courier insists that you seal the packet in their presence after they check it for explosives and drugs? The T-Cognition system is a terahertz scanner developed by researchers at the Fraunhofer Institute for Physical Measurement Techniques IPM in Kaiserslautern in collaboration with Hübner GmbH & Co. KG in Kassel, which helps scan the content of packages or envelopes without having to open them. In specific, the system helps recognise parcels containing hazardous, flammable materials such as explosives and illicit drugs.
The scientists chose to use waves in the terahertz range for scanning, because this lies midway between microwave and infrared in the electromagnetic spectrum, and thus combines the advantages of both. These low-energy frequency waves can easily penetrate paper, wood, lightweight fabrics, plastics and ceramics. The characteristic spectra generated by them can be analysed using intelligent software to accurately detect the type of material they travel through. Also, since terahertz waves are non-ionising, they are safe to use without any special shields.
Although very useful for mail scanning, this nascent technology can also be used for other security applications such as industrial security, airport security, and so on.
New light for scouting fingerprints
When we say tech in security, it is not just about high-tech video surveillance and cloud-based analysis. Sometimes, simple breakthroughs can be big, such as this new UV light developed at the University of Leicester to identify fingerprints on thermal paper used for printing receipts, ATM bills, etc—a key requirement for solving several financial crimes.
Historically, it has been a challenge to visualise fingerprints on thermal paper, as the solvent used in the chemical process turns the whole paper black. A technology called Hot Print System (HPS) developed some years ago helped read fingerprints on thermal paper by applying heat to the paper; however this too turned out to be problematic as the quality of thermal paper varied from country to country.
This new technology, on the other hand, uses a specifically-tailored UV light to illuminate the thermal paper and create faint images of fingerprints. This enables quick, non-invasive and speculative examination of fingerprints. The fine images produced by the UV light can then be enhanced and converted to digital form using the earlier HPS system.
Knowing you intrinsically
People you are close to do not need an ID to recognise you! They know you by who you are, what you do, and why you do things. Considering that the mobile phone has now become many a man’s closest confidante, have you ever wished your phone too could recognise you instinctively, without needing a password? Perhaps they could, in the future, thanks to a new security system developed by researchers at the Georgia Institute of Technology.
The new system continuously monitors how a user taps and swipes a mobile device, and tries to understand the patterns in these movements. If a stranger uses the device, the system recognises that the movements do not match the owner’s normal tendencies, and can be programmed to take further action such as locking the device or alerting somebody.
Called LatentGesture, the system was tested at the lab using 20 users. As the users do various tasks like tap buttons, swipe sliders or check boxes, LatentGesture develops a profile of each person, what they call a person’s ‘touch signature.’ For every device, the system can store five touch signatures–the owner’s and four authorised users’. Whenever somebody uses the mobile device, it automatically identifies whether it is the owner or one of the other authorised users, and allows all operations they are authorised to do. If a stranger uses the system, an alert is issued or the device is locked. The system, tested on Android devices, was nearly 98 percent accurate on a smartphone and 97 percent correct on tablets.
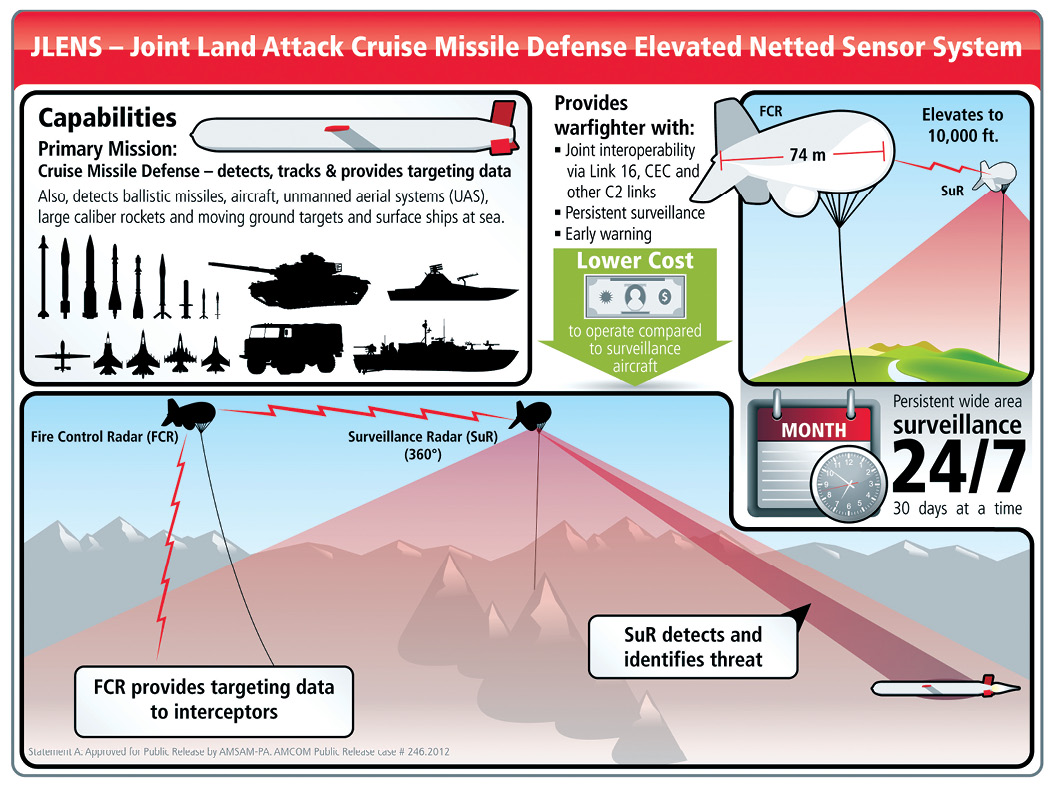
Funny looking blimps, serious about security
Early this year, the US Government announced that it would be deploying two giant security blimps over Maryland around October. The blimps would carry out 24/7 domestic aerial surveillance and help enhance security manifold.
Developed by security major Raytheon, the Joint Land Attack Cruise Missile Defense Elevated Netted Sensor System (JLENS) comprises two 243-foot long aerostats flying 10,000 feet above the ground. One of them has 360-degree surveillance capabilities that enable it to see as far away as 547 km in any direction, while the other has a powerful integrated fire-control radar system. The two aerostats are connected to mobile mooring stations on the ground using tethers that have high-speed fibre-optic cables for sending data as well as transmitting power. The aerostats can also communicate via radio links.
Of course, this announcement has triggered a lot of uproar about privacy concerns, but the government is confident that the two aerostats would work hand in hand to effectively spot and ward off threats.
Human-like, real-time facial recognition
A tool that excels in facial recognition and biometric identification is perhaps what we need to replace the security guard, but how efficient are today’s facial recognition tools. It is said that Facebook’s facial recognition has near human efficiency, but that is for static images. For real security systems, we need real-time facial recognition. Many companies and research firms are working on such technologies today, and one such example is FST Biometrics (erstwhile FST21), founded by Major General Aharon Zeevi Farkash, the former head of the Israeli Military Intelligence Directorate.

One of their base technologies for In Motion Identification (IMID) is SafeRise, which uses a combination of real-time facial recognition and biometric technology. When somebody walks up to a secured area, the system is capable of immediately recognising whether she is an authorised person or an intruder, without even requiring the person to stop near a camera or provide fingerprints, iris prints, or any authentication.
Mostly, the system relies on facial recognition. Using a profile picture, it tries to understand a person’s unique features, such as say, the number of pixels between her eyes. Then, every time that person approaches a protected area, the SafeRise system tries to compare all the special features it has stored. If you watch the output of the security camera, the software puts a yellow box over anything that registers as a face. If it recognises the face, the box turns green, else it turns red and the door remains locked. As the system ‘watches’ the person more, it assimilates more biometric details about her including her gait and voice. The more it learns about the person, the faster it identifies the person. SafeRise is incorporated into FST products like the Digital Doorman.
Quantum leap in mobile phone security
Considering the amount of transactions people are conducting using mobile devices, researchers have now started considering mobile security on the same lines as banking security! A team at the University of Bristol, in collaboration with Nokia, recently demonstrated how quantum cryptography using Quantum Key Distribution (QKD), a bulky and expensive technique currently used for securing fixed physical locations like server rooms in banks, could be used to implement an ultra-high security scheme for mobile devices. New hope comes from the team’s efforts to reduce the bulky and expensive resources required for quantum cryptography, so that it can be implemented by simply integrating an optical chip into a mobile handset.
This is basically a client-server QKD scheme, wherein the cumbersome equipment, such as the laser and detectors, are located at the server side and are accessible to a client over a communication network. The client only requires an on-chip polarisation rotator, which may be integrated into a handheld device. While the experiments seem successful, the team is now working towards implementing the client-server QKD system in a real communications network.
More examples, all around us
There are lot more interesting developments in security across the world—and most of them accurately reflect the changing mindsets of people and the newer threats of networking, increased mobile usage, cloud computing and the Internet of things. For example, a decade ago people would not have thought of do-it-yourself customised home security using sensor-software kits but today people need it to protect their privacy and changing lifestyles. Likewise, nobody would have even imagined that it would become necessary to protect trivial devices like, say, the printer. But, with almost all devices getting connected to the corporate or home network, every device becomes a point of vulnerability.
The threats faced by people today are much more—thanks to the technologies that seemingly promise to make life easier for them, and that means more sleepless nights for technologists paving the way for security X.0!







