In his book Cybershock, Winn Schwartau mulls over some possible effects of a well-orchestrated electromagnetic pulses (EMP) attack upon Western infrastructure. Wall Street or other banking systems could be attacked, resulting in successive failures and huge financial losses. Aircraft avionics and guidance systems could be overloaded by targeted high-energy radio frequency, leading to potentially fatal conditions.
Medical equipment could malfunction under the attack of intense energy spikes, putting several human lives at risk. Municipal emergency services could be terminated by devastating wide-band microwave jamming, and power lines and transformers could act as highly-efficient conductors to transmit massive currents to businesses and sub-stations, leading to regional blackouts.
Terrorism is the unlawful use of force or violence against persons or property to intimidate or coerce a government, the civilian population or any segment thereof, in furtherance of political or social objectives. Terrorist groups are becoming international, dedicated, organised and structured and, year after year, emerging as a big threat to peace and prosperity. They are relying increasingly on technology to become more lethal, dangerous and difficult to combat.

Their motives are not limited to political but include religious or ideological objectives, too. Modern technologies are being adapted to effectively coordinate and support their activities, collect money and spread information and propaganda. For example, using IT and the Internet, terrorists have developed sophisticated and versatile communication techniques. Bill Clinton, former president of the USA, once stated, “Our security is challenged increasingly by non-traditional threats from adversaries, both old and new, not only hostile regimes, but also international criminals and terrorists who cannot defeat us in traditional theaters of battle, but search instead for new ways to attack by exploiting new technologies and the world’s increasing openness.”

Current technologies being used to combat terrorism
There is an urgent need for leveraging internationally the expertise and research programs to develop new and improved technologies to combat terrorism. This is expected to help prevent terrorist attacks and provide militaries with improved capabilities to detect, disrupt and pursue terrorists.
There is also a need to provide the capability to deal with the effects of chemical, biological, radiological and nuclear weapons. Presently, various technological tools and techniques have been deployed to combat terrorism. Some of these technologies are fairly mature, while others show great potential but still require some years of research and development before these are fully operational.
Yet, all technologies share a common characteristic; these offer significant potential solutions to address the most pressing anti-terrorism concerns.
The technologies are:
• Directed-energy weapons
• Non-lethal weapons
• Nanotechnology
• Biometrics
• Data mining and analysis technologies
• Network-centric operations
Directed-energy weapons.
These weapons generate very high-power beams such as lasers and microwave radiations that are precisely focused to hit targets with sub-atomic particles, both to track and destroy.
Directed-energy weapons have the capability to cause casualties, damage equipment, disable targets on ground, air and sea, and provide active defence against threats from artillery, rockets, mortars, missiles and unmanned aerial vehicles.

Non-lethal weapons.
These are employed to incapacitate personnel or material while minimising fatalities and undesired damage to property and environment. Their functions include preventing or neutralising the means of transportation such as vehicles, vessels or aircraft including those for weapons of mass destruction.
The technologies used include acoustics systems, chemicals, communications systems, electromagnetic and electrical systems, entanglement and other mechanical systems, information technologies, optical devices, non-penetrating projectiles and munitions, and more. These can be integrated with systems to make these more effective and discriminate.

Nanotechnology.
Nanotechnology involves developing materials and complete systems at atomic, molecular or macromolecular levels where dimensions fall in the range of one to 100 nanometres. Fabrication at such nano scale offers unique capabilities, and materials can be made to have specific properties.
Among anti-terrorism applications, sensors using nanotechnology are most important. Nano-scale sensors form a weak chemical bond with the substance and then change their properties in response (such as colour change, or a change in conductivity, fluorescence or weight). As an anti-terrorism tool, nanotechnologies are relatively in their infancy stage vis-à-vis other technologies.
Biometrics.
This refers to recorded unique physical or behavioural characteristics of individuals. These are more reliable and more difficult to forget, lose, get stolen, falsified or be guessed. Biometrics can be used for verification or identification. For identification, a person’s presented biometric is compared with all biometric templates within a database.
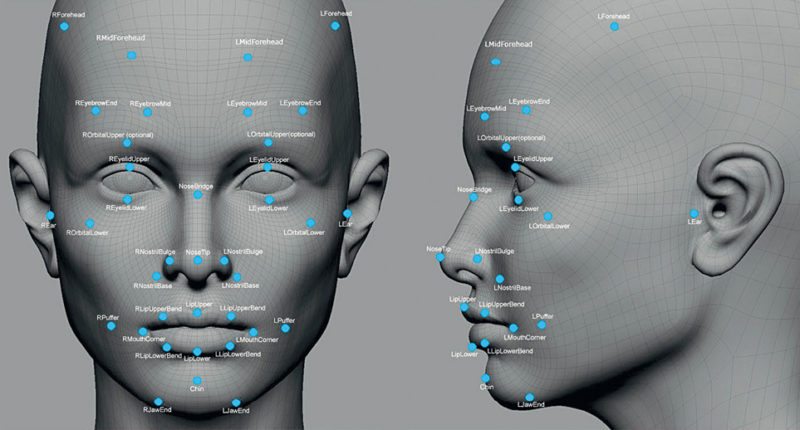
Five major types of biometric technologies available today are:
1. Iris recognition that relies on distinctly-coloured ring surrounding the pupil of the eye
2. Hand geometry that relies on measurements of fingers, distances between joints and the shapes of knuckles
3. Fingerprint recognition that relies on features in the impressions made by distinct ridges on fingertips
4. Face recognition that identifies individuals by analysing facial features such as the upper outlines of eye sockets or sides of the mouth
5. Voice recognition that is based on the differences in voice

Data mining and analysis technologies.
Data mining and analysis technologies are used for analysing historical and current online data for prediction and description by identifying patterns and anomalies from the vast database.
Prediction involves using variables in the database to predict unknown or future values of other variables of interest.
Description involves increasing knowledge about a variable or dataset by finding related information to obtain human-interpretable patterns describing the data.
The trail of terrorists is often indistinguishable from mass commercial and government data. Traditional investigation techniques follow an intricate process of seeking out information related to an individual. This becomes increasingly problematic as more and more information becomes available.
Network-centric operations.
These operations increase the operational effectiveness and efficiency by networking sensors, decision makers, law-enforcement agencies and disaster managers to achieve increased speed of operations, increased security and safety, reduced vulnerability to hostile action and self-synchronisation. Systems from local to national levels can be integrated into a network to address anti-terrorism.
How terrorist groups are using IT
Terrorist groups all over the world are widely using IT for various functions such as internal communication and coordination, propaganda and misinformation, recruitment and financing, information and intelligence gathering with the final objective of spreading hate and violence.
Islamist terrorist group Al-Qaida created by Osama Bin Laden relies heavily on computers and other modern communication tools. By the early 2000s, Islamist terrorists had started using chat rooms, pornographic sites and other Internet utilities to masquerade maps and photographs of their targets, and for sharing directions and information for their operations.

US officials stumbled upon messages that were encoded using free encryption programs set up by Internet privacy groups. Images were formed via a series of dots inside which were strings of letters and numbers that computers could read to reconstruct images. These are just a few examples of how IT has been used by terror groups.
Irish terrorists took help of contract hackers to penetrate computers to get the home addresses of law-enforcement and intelligence officers. In March 2000, an investigation by Japanese police forces showed that a software system had been bought by Aum Shinrikyo cult, which is notorious for poisoning Tokyo subway in 1995. This software system was used to monitor more than 100 police vehicles, and was also sold to several Japanese companies and government agencies, thus, making them vulnerable to cyber attacks by this cult group.
Today, terrorists from the infamous ISIS group meet openly on Facebook or Twitter. They ensure their discussions remain highly confidential by using encryption technology to encode their messages. ISIS has a technology cell that consists of five to six members offering 24/7 support on encrypting communications, disguising personal details and using apps like Twitter while avoiding surveillance.
ISIS is known to use an app called Telegram, which offers two layers of encryption, and claims to be faster and more secure than the more commonly-used WhatsApp.
The issue of hunting out terrorist communication is almost like finding a needle in a haystack. It is not possible to scan every voice call, message or email, given the very high volume of communication. Then, there are problems related to the right to privacy and confidentially of certain communication such as business plans and banking transactions.
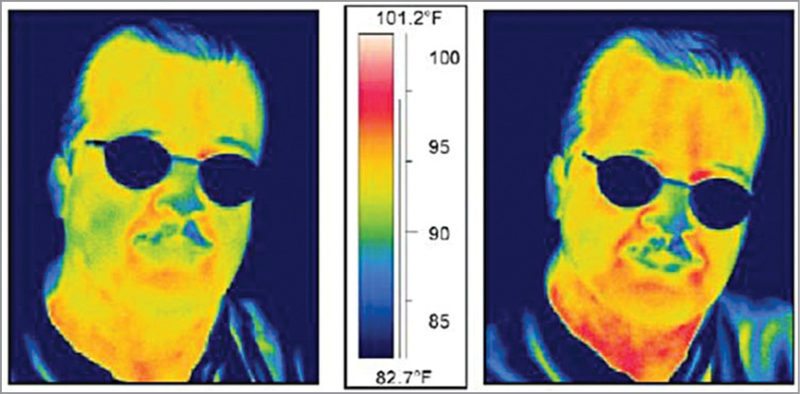
Safeguard technologies for the future
Current levels of technology available are actually inadequate to deal with the scope and potential severity of the terrorism threat. You need to always remain one step ahead of the terrorists and develop security systems that are capable of protecting the public, safeguarding their liberties, travel and commercial activities, in a proactive manner. This requires vision, strategy and optimisation to enable selecting the most crucial technologies capable of providing maximum security for the resources invested. Utmost flexibility to address a wide range of threats is also required.
Aviation giant Boeing and other major aircraft manufacturers together are in process of developing a remote-control technology for flying a commercial aircraft. Had this technology been available in 2001, perhaps the 9/11 terror attacks on World Trade Center and Pentagon that killed nearly 3000 people could have been prevented.
Biometrics.
There is research and development work going on for useful biometric options that include vein scans, facial thermographs, DNA matching, odour sensing, blood pulse measurements, skin-pattern recognition, nail-bed identification, gait recognition and ear-shape recognition.
The surest way to stop terrorists from hijacking or bombing planes from within is perhaps to stop attackers from boarding the planes in the first place. Hence, researchers have also envisioned combining sophisticated video surveillance at airports with software that analyses, for example, facial expressions for signs of lying. Researchers are also developing devices that can remotely scan for irregular blood pressure and heart rates, to serve as supplementary data.
Clothing.
In the future, it is possible that flight marshals and crew would be adorning uniforms that also serve as body armour. A team of chemical engineers is researching the possibility of developing a thin but super-strong fabric by bonding 300 alternating layers of clay and polymer.
Some scientists in the USA, Europe and China have joined ordinary cotton with super-hard boron to create a boron nano-tube fabric that is light and flexible enough to be put on as an undershirt, and could even shield the body from a bullet.
Robust hashing.
Robust hashing is an innovative futuristic tool against online video of violence, beheadings and anti-Western criticism that are used to get new people into the terrorists’ fold, and extend hate and violence.
These videos are being widely used by groups such as ISIS and Taliban. These are multiplying at lightning speed on social media sites. A software tool is being developed that creates an exclusive fingerprint for any video that can be used to automatically find copies as soon as these are uploaded, and this does not require human intervention or judgement.
Videos get edited or even altered. For example, an advertisement may be inserted making the video a little longer. However, the new technology beats that since it works by matching little snippets of the video. Once a video has been tagged as related to terrorism by a viewer, a robust hash is created and positioned in a database, overseen by Counter

Extremism Project.
This database is used by various social media sites such as Facebook and Twitter so that they can automatically prevent uploading of this content.
While today several online and social media services are removing terrorism-inciting videos manually, it is hoped that in time to come it will be done automatically, making the whole process much more efficient and effective.
However, such software comes with its own problems since it can also automatically erase harmless videos such as a clip from a movie that has violence. Also, one man’s terrorism could turn out to be another man’s social protest.

Endpoint
The terrorist threat against the free world is global, serious, challenging and persisting. The means and technologies that are practical, affordable and can counter the serious threat of terrorism are required to be developed using joint efforts globally.
There are many impediments and challenges such as the tremendous expenditure involved, given the high cost of procuring and adopting a technology and scarcity of required resources, especially human skills as well as facilities and equipment. Any new technology may also create unintended consequences, bring unexpected liabilities, and produce environmental pollution and adverse public reactions.
Also, new technologies and systems will have significant training and leader development challenges. Obstacles to creating anti-terrorism technologies that are steps ahead as compared to those used by terrorists are many. Hence, various countries need to create a vision and develop policies that will help overcome the barriers to innovation.







