Tiny wireless devices and the enormous growth of wireless communication technologies have already established the stage for large-scale deployment of wireless sensor networks (WSNs). A typical WSN consists of a large number of small, low-cost sensor nodes, which are distributed in the target area for collecting data of interest. Most of the time, WSN is used for monitoring, tracking and event management related applications. WSN is not a new topic as many inventions have been done and countless applications have been successfully implemented.
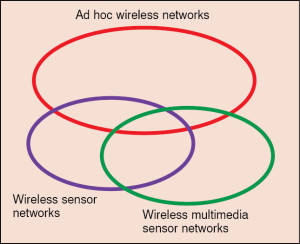
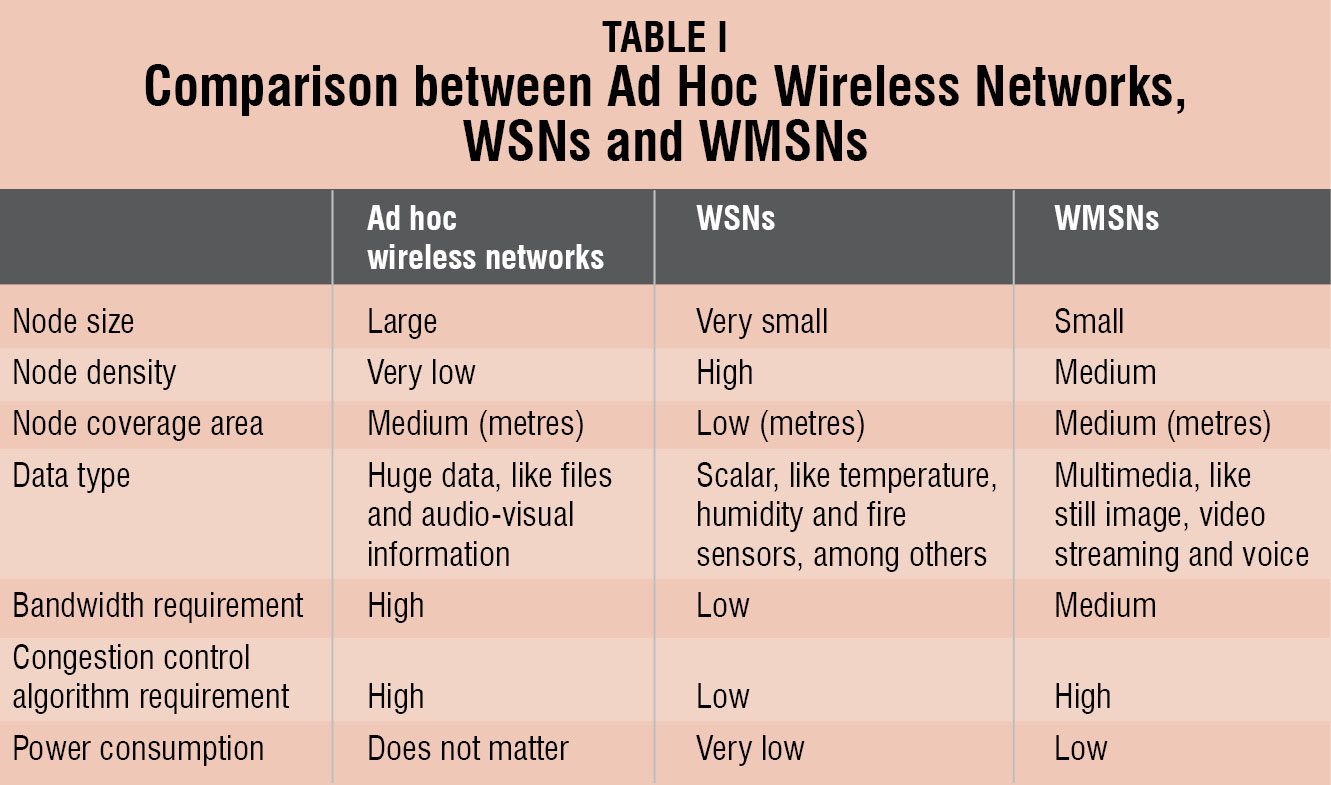
Fig. 1 and Table I show the similarities and differences between ad hoc wireless networks, wireless sensor networks and wireless multimedia sensor networks (WMSNs). All these networks are used for small-scale and medium-scale networks that do not require a fixed architecture and can be deployed temporarily. WMSN requires a novel architecture, and the advanced protocol design and algorithms need to be implemented to fulfil the criteria. This article exposes the internal structure of the multimedia sensor node, architecture of WMSN, their challenges, research opportunities and applications.
Internal structure of the multimedia sensor node
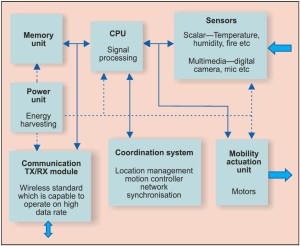
Normally, a multimedia sensor device includes a sensing unit, processing unit (CPU), communication module, co-ordination sub-system, storage unit and an optional mobility/actuation unit. Sensing units usually have two sub-units: sensors [digital micro cameras, microphones and/or scalar sensors (for example, temperature sensors, humidity sensors, fire sensors, pressure sensors and gas sensors)], and analogue to digital converters (ADCs). Most of the sensors generate analogue signals which should be converted into digital form by using ADCs as these are to be fed into the CPU.
 The CPU executes the system software in charge of coordinating sensing and communication tasks for signal processing, and it is interfaced with a storage unit. A communication Tx/Rx module interfaces the device to the network. In many applications, it has been observed that around 70 per cent of the battery is consumed for transceiver processes and the remaining 30 per cent consumption includes computational tasks, signal processing, co-ordination systems and sensor sub-units.
The CPU executes the system software in charge of coordinating sensing and communication tasks for signal processing, and it is interfaced with a storage unit. A communication Tx/Rx module interfaces the device to the network. In many applications, it has been observed that around 70 per cent of the battery is consumed for transceiver processes and the remaining 30 per cent consumption includes computational tasks, signal processing, co-ordination systems and sensor sub-units.
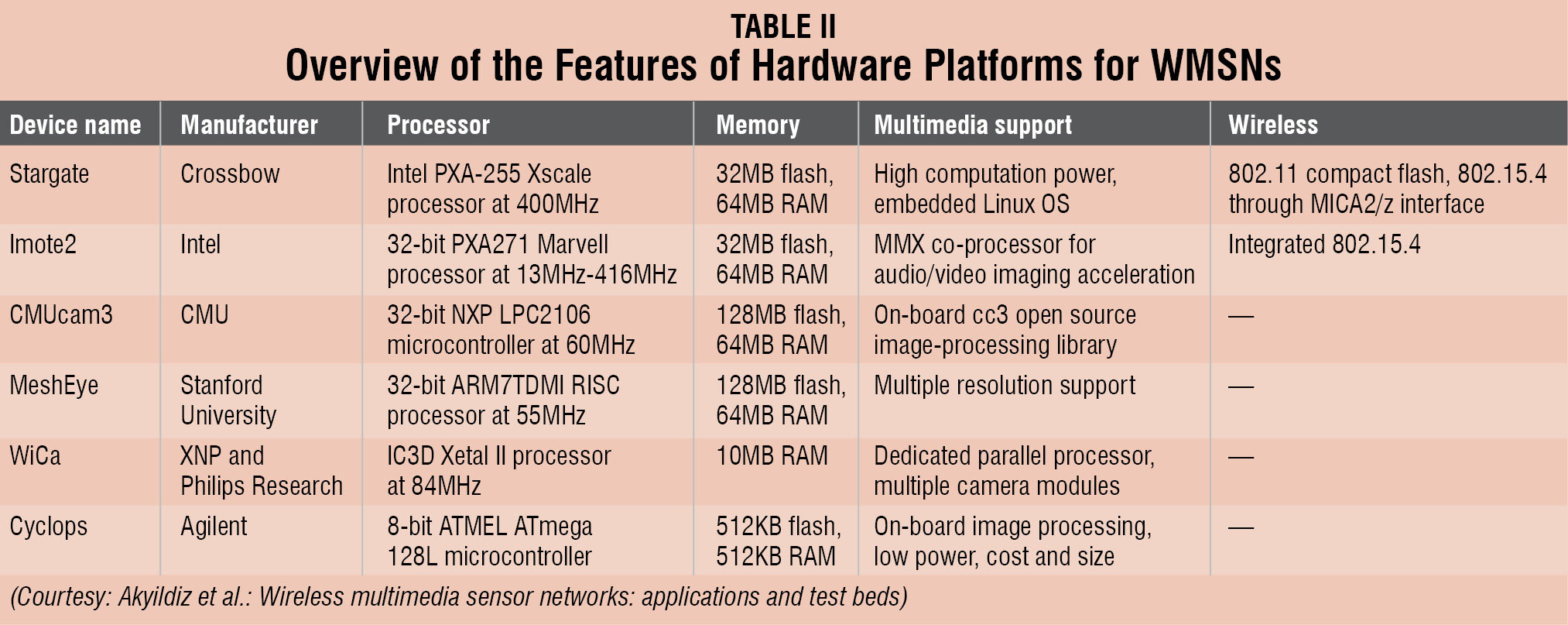
A coordination sub-system coordinates the operation of different network devices by performing various tasks, such as network synchronisation and location management. A mobility actuation unit can enable the movement or manipulation of objects, like motor, to track the object. The whole system is powered by a compact power unit that may be supported by an energy-scavenging unit, such as solar cells. Table II gives an overview of the features of hardware platforms for WMSNs.
WMSN architecture
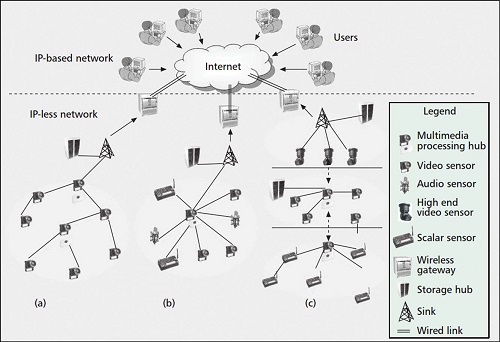
Fig. 3 shows the reference architecture of a WMSN, which is classified as single-tier and multi-tier architecture. Before we discuss further, it is important to know about the functionality of all components used in this architecture.
Standard audio and video sensors capture sound, still or moving images and videos of low resolution. Scalar sensors are another type of sensors that sense scalar data and physical attributes, such as temperature, humidity and pressure, and report measured values to their cluster head. These are typically resource-limited devices in terms of energy consumption, memory storage and processing capabilities.
Multimedia processing hubs behave as cluster heads. These devices have comparatively large computational resources and are suitable for aggregating multimedia streams from individual sensor nodes. This can be done by various algorithms implemented in it. Algorithms are capable of managing flow of control (frames per second) by adding and discarding frames. Finally, it is capable of reducing both the dimensionality and volume of data conveyed to the sink and storage devices.
The storage hub allows data mining and feature-extraction algorithms to recognise essential characteristics of the event, even before the data is sent to the end user. The sink is a common data-gathering point of IP-less networks. It also supplies filtered data to the user at the remote end, gathered by a WMSN. Multiple sinks may be required in a large or heterogeneous network.
The gateway creates a bridge between an IP-less network and IP based network. It is an IP-addressable component of the WMSN. It gives permission to the user to monitor and control the WMSN from a remote location as it has an IP address and the capability to create a connection with the Internet.
At the end, users are at the highest end of the hierarchy. They are typically identified through their IP addresses and run application-level protocols and software that assign queries and display results obtained from the WMSN.
Single-tier means the network is without hierarchy, and cluster is directly connected with the sink. Figs 3(a) and 3(b) show a single-tier architecture, which can be arranged in a flat or clustered manner. Flat topology means all nodes have essentially the same role.
In cluster topology, a group of nodes form a cluster, and the geographical target area is divided into numbers of clusters. Each cluster has one cluster head and one cluster member. In a cluster, two members cannot communicate directly, as shown in Fig. 3(b).
All cluster members send data to the cluster head, and hence the cluster head has the highest priority to allocate the channel for further communication. For any cluster member, inter-cluster and intra-cluster communication takes place via the cluster head.
Node with the highest energy is selected as cluster head as it consumes more energy. Special algorithms and protocols (for example, LEACH) elect the cluster head on the basis of remaining battery life (RBL) of all nodes within the cluster. A cluster that includes a variety of sensor nodes is called a heterogeneous cluster sensor network (Fig. 3b).
A multi-tier architecture is arranged in hierarchy or multiple layers. As shown in Fig. 3(c), one cluster has formed of scalar nodes and the other using video sensors. Both clusters forward the data to the sink through high-end video sensors. The sink is connected to the Internet (IP based network) via a wireless gateway. This way the user can monitor and control targeted areas from a remote location.
Challenges and opportunities
High data rates. WMSNs require high data rates as data is in terms of live video streaming, audio and still images. Achieving high data rates (in terms of Mbps) on available narrow channels is a challenging task. Recently, researchers started to implement ultra-wide band (UWB) technology on sensor nodes for higher data rates.
Signal detection and estimation. Signal detection, estimation, filtering, data gathering and wireless channel separation are still open research challenges for the implementation of WMSNs. Researchers have proposed OFDMs (frequency-division multiplexing schemes) to increase data rates and remove interference between two wireless channels.
Reliability. High information assurance is expected in WMSNs, and for that effective error detection, correction code with accuracy, robustness, resiliency and retransmission policy need to be found out.
Energy efficiency. Nodes have limited battery and, for most applications, charging and replacement of the battery is not possible. Nodes need to serve for many years. To reduce power consumption, researchers have already started designing and implementing different types of MAC protocols [real-time independent channels (RICH) MAC protocols, frame sharing (FRASH) MAC protocol, cluster based on demand multichannel MAC protocol, Q-MAC, RL-MAC and many more]. Energy efficiency can be obtained by implementing new algorithms on the physical layer (modulation techniques, architecture, etc) as well as on the MAC layer. Many image- and video-compression algorithms are also introduced, for instance, distributed video coding (DVC), high-efficiency video coding (HEVC), discrete cosine transform (DCT), discrete wavelet transform (DWT) and curvelet transform. Results show that by using advanced compression techniques, energy consumption can be reduced by up to 50 per cent.
Inherent uncertainty. In most WSNs, mobility of nodes creates problems as it affects topology, routing protocols and synchronisation. Coverage area and coherence bandwidth depend on moving obstacles and the surrounding environment.
Security and privacy. Multimedia industrial monitoring and control kind of applications require high privacy and security. Unauthenticated persons should not be able to access private data.
Quality of service (QoS) and quality of information(QoI). High QoS and QoI are required on each and every communication layer. The resolution should be good enough at remote places. For video streaming, 5fps to 20fps (frames per second) is expected for better quality, and all layers should be designed accordingly.
Applications
WMSNs have numerous killer applications. Multimedia surveillance sensor networks can be used to enhance and complement existing surveillance systems to prevent crime and terrorist attacks. These can be used to locate missing persons, identify criminals or terrorists and record other potentially relevant activities, such as thefts, car accidents and traffic violations. With the help of WMSNs, it will be possible to monitor car traffic in big cities and on highways that offer traffic-routing advice to prevent congestion or identify violations.
WMSNs play a vital role in personal health care units. Telemedicine sensor networks can be integrated with 3G and 4G mobile networks to provide ubiquitous health care services. Patients can carry various types of medical sensors to monitor different parameters, such as blood pressure, ECG, breathing activity, pulse oximetry and body temperature. Remote medical centres or personal doctors can monitor the condition of patients to infer emergency situations. This will be more beneficial for villages and rural areas where doctors and health centres are not available all the time.
WMSNs can also be used for environmental and structural monitoring purposes. Video and image sensors may be used to monitor the structural health of bridges and other civil structures. In industrial applications, WMSNs can give visual inspections and automated actions.








What is the maximum capacity for the memory unit