The CEC1702 full-featured microcontroller streamlines security implementation for an increasingly connected world
17 March 2017 [NASDAQ: MCHP] — The CEC1702 hardware cryptography-enabled microcontroller is now available from Microchip Technology Inc., a leading provider of microcontroller, mixed-signal, analog and Flash-IP solutions. The CEC1702 addresses the increasing need for security measures, such as secure boot, driven by the continual growth of Internet of Things (IoT) applications.
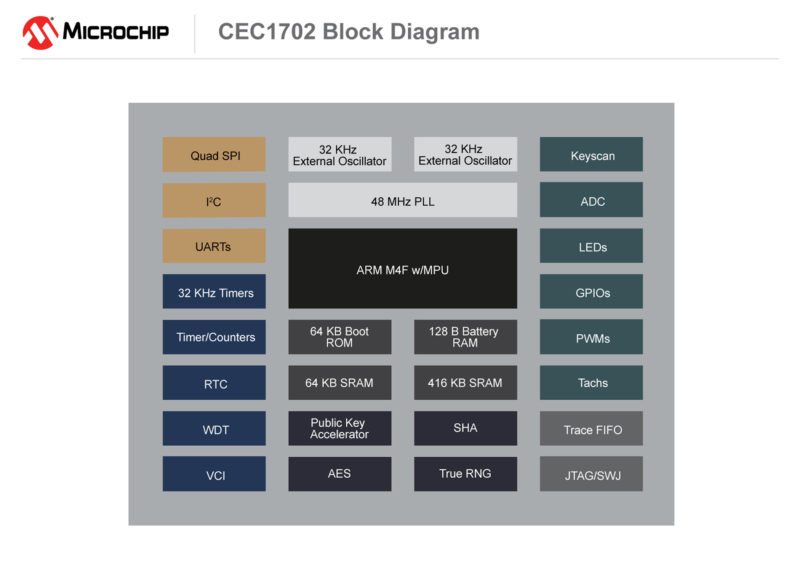
The CEC1702 is a full-featured ARM Cortex-M4-based microcontroller with a complete hardware cryptography-enabled solution in a single package. This low-power but powerful, programmable 32-bit microcontroller offers easy-to-use encryption, authentication, private and public key capabilities and allows customer programming flexibility to minimise customer risk. The CEC1702 also provides significant performance improvements when compared to firmware-based solutions. The device’s hardware cryptographic cipher suite reduces compute time by orders of magnitude over software solutions, and, as an example, provides 20x-50x performance improvement for PKE acceleration as well as 100x improvement for encryption/decryption. This robust hardware-based feature set results in applications that can run security measures quickly, effectively and with significantly lower cost and power consumption.
Protecting system integrity has never been more important. Whether it’s being used as a security coprocessor or a standalone microcontroller, the CEC1702 delivers a multi-dimensional defense against attacks, including:
· Pre-boot authentication of system firmware: Providing an immutable identity and a root of trust to ensure that the firmware is untouched and hasn’t been corrupted
· Firmware update authentication: Verifying that the firmware update has not been corrupted and is from a trusted source
· Authentication of system critical commands: Attesting that any system-critical command is from a known source with authorisation to make the given change, preventing potentially devastating actions
· Protection of secrets with encryption: Safeguarding code and data to prevent theft or malicious activities
“The acceleration of the Internet of Things has brought higher visibility to the security considerations of new designs,” said, Ian Harris, vice president of Microchip’s computing products group. “One of the hardest challenges to solve in a connected system is the ability to ensure that the boot code has not been comprised. The CEC1702 eliminates this issue by making it easy for designers to verify pre-boot authentication and then provide firmware updated from known, trusted resources.”