“Computers in the future may weigh no more than 1.4 tonnes.”
—Popular Mechanics, 1949
“There is no reason anyone would want a computer in their home.”
—Ken Olson, president, chairman and founder of Digital Equipment Corp.
The two quotes show us how unpredictable the future is and that we probably have no idea what is in store for us in terms of the size, power, capabilities, etc of computers in, say, 50 years from now. However, let us try and imagine how computer technology is likely to shape up in about 15 years. Let us try and be as creative as possible to paint a possible future scenario, perhaps based on our wish lists, needs and fantasies.
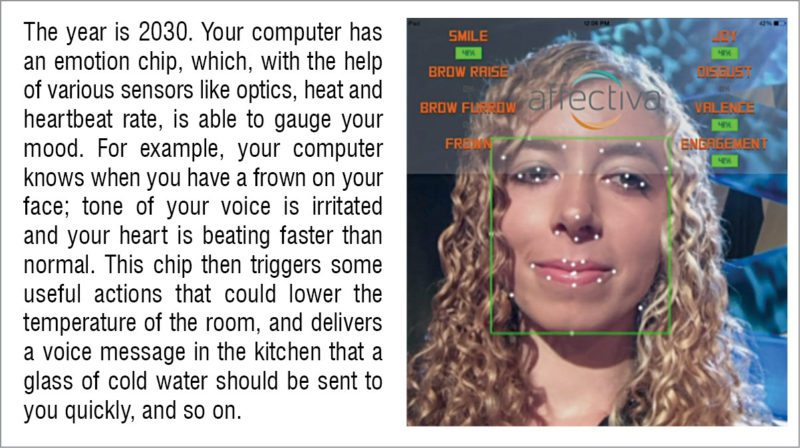
Computers with an emotion chip could find their way into everyday things used by us. For example, your mirror could sense that you are in a bad mood, communicate this to your best friend and request her to give you a call to comfort you.
Your personal network
In the future, it is expected that a strong personal network will evolve. Mostly, the personal network will comprise one or more computing devices in communication with one another with the help of various permanent and transient communication links. One or more devices would be very high-end laptops—the basic portal through which you, as a user, will access the network. Once disconnected from the personal network, this portal will work just like a standalone device.
The speed of wireless Internet would be so high that actual computing and data processing will not be on your personal device, but on a far off, more powerful machine connected via the Cloud. Such a technology will enable you to process data at lighting speeds. For example, you could be researching the way proteins take certain shapes, called folds, and how that relates to what proteins do.
This problem that typically takes months at present will be completed in just a few seconds. Problems could range from breaking codes to searching data sets and even extend to the creation of new materials.
Now, close your eyes, step into the time machine and take yourself to the 2030s. Your personal network has notified the navigation computer in your car about your departure time and destination, today morning. Just as you are backing out of the driveway, the navigation computer is informed of a traffic jam, and it informs you of an alternate route, estimates your new arrival time, notifies your office staff of your situation and reschedules your early meetings.
You are now driving to work. However, you are also able to do various tasks such as read the newspaper, talk on the mobile phone with your business associate in Mumbai, or use your laptop—just as safely and conveniently as train or bus commuters do. A combination of expressway sensors, global-positioning systems and in-car computers are actually doing the driving for you on limited-access roadways. Your car PC provides door-to-door driving instructions and routes you around accident sites. It even finds restaurants and books hotels on vacations for you.
You arrive at your office and settle down at your desk, your personal network links with your wife’s personal network to get her arrival schedule (she is away on a business trip to Kolkata) and to make a dinner reservation at your favourite restaurant. As you prepare to leave work, your personal network replicates the information that you need to take home, synchronises calendars and learns that your wife’s flight is about half-an-hour late. It reschedules the dinner reservation and also notifies your car.
Tomorrow’s personal networks will be as invisible to you as, say, the networks that work quietly in the back-end to provide the Internet to residences. And generally, the networks will require little intervention during operation.
In a traditional PC, the CPU, memory and I/O devices are linked via one or more buses, that is, paths in circuits that provide the communications link, making it feasible for the different components of the PC to share data. In the personal network, the network itself is actually the bus. Network architecture allows data flow in any and all directions, with individual computers fully aware of the network and its constituents.
Like the members of a cricket team interacting with each other during play, member devices in the network will often work together. Just as players come to play individually, each network device will operate some of the time without linking to other devices in the network. Some of these individual devices within the personal network will be dedicated to you, their owner, whereas, others will be shared with other users, via their personal networks.
Similarly, primary means for you to access the personal network will be a portable computing device resembling a high-end laptop that will be dedicated to you. Other parts of the network can include computing devices embedded in your home, in your appliances or in your car. It is inevitable that your family members will have their own personal networks and, hence, some of these individual devices could be part of multiple personal networks.Various servers, which are relatively powerful computers that anchor the network by performing computationally-intensive services for less powerful computers on the network, will manage the personal networks and their data stores. These servers will be shared among a number of personal networks, but individual personal networks will remain logically separated.
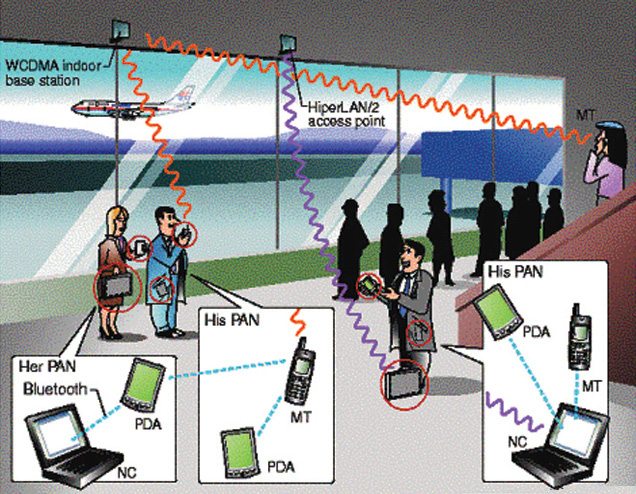
The personal networks can connect among themselves, especially those of family members, friends and groups having a common interest or those who are together in a shared environment such as home or office, thus making the system very powerful. A combination of wired and wireless communications makes it possible to establish links to any personal network anywhere in the world, if required.

Some challenges
One of the biggest technology challenges is the user interface. The personal network is required to communicate with people in a human-to-human manner, which comes naturally to us. It means making adjustments as per our computer literacy. Also, voice identification and speech synthesis by the computer are some areas on which a lot of research is happening. There are many complexities such as speech patterns that could change for the same individual depending on his or her mental condition, mood, physical health, etc.
Speech recognition is based on identification of phonemes—the smallest acoustical components of language, and spoken English comprises approximately 80 phonemes. Human speech is sampled by the computer with digitised audio signals and compared with those that it has stored. There is some scope to accommodate disparities in individuals’ pitches and word duration. In addition, probability of a particular word following another will lead the computer towards finding a match. Finally, the need is that you should be able to interact with your personal networks simply by talking and listening to these.
Apart from human-to-machine communication, reliable machine-to-machine communication is also important, especially if the personal network is to be able to interact effortlessly with other people’s personal networks. Channels of communication comprise chiefly the physical links between machines like home LANs, infrared links among devices located in very close proximity, short-range radio links used in cordless phones, long-range radio links as in mobile phones and cable or high-speed connections to the rest of the world.
Wireless communication techniques form the hub to the personal network mobile computing. While for in-room communication infrared systems offer links of up to 4Mbps across a distance of about one metre, wide-area usage demands radio links.
Complexities of wireless communications are far greater than those posed by wired links. Key communication parameters such as transmission speed, error rate, reliability and delay can change considerably and rapidly during the course of a single wireless communication. This instability is driven by the variability of radio frequency noise and the signal attenuation that is caused by natural phenomenon such as storms or due to interference from various electronic devices.
Mobility further brings in more uncertainty. For example, radio-wave propagation is abruptly interrupted when a skyscraper, vehicle or some other large object comes between the transmitting and receiving devices. Therefore transmission speeds available in wireless communications tend to be much lower vis-a-vis wired links.


Security issues
Access to personal network devices will be increasingly protected by biometrics—use of physiological features such as pattern of a voice, fingerprint or iris to permit activation. Biometrics are unique to an individual. For example, no other human being on Earth has the same fingerprint as yours and, hence, your thumb or finger swipe allows you and only you to access your laptop.
Traditional protection such as passwords will exist but only to supplement biometrics. However, public-key cryptography—a mathematical system that will be used to secure owner control over the personal network and allow for intra- as well as inter-network privacy—will form the hub of the security system. Encryption systems known as RSA and PGP are examples of public-key cryptography.
Public-key cryptography works by assigning each person two different keys, which really are two numbers linked with each other. The two keys are several digits in length and next to impossible for most humans to memorise. These are generally saved on the computer’s hard drive or on a disk. The public key is accessible to anyone who wants to send you a secure message. The private key, however, is only available with you. Public-key cryptography guards with encryption and ensures privacy. A sender can encrypt a message to you that could be an account number or a debit card number using your public key. However, this message can be decoded only by using both the public and the private key, and only you have the private key.
Other issues
Apart from security, another critical aspect is software. Programs need to be such that these cater to multiple computers and operating systems. Software will need to be written in a language like Java that can translate commands into readable instructions and is device agnostic. Maybe one of the biggest challenges to the development of the personal network (as it is also for the most sophisticated and high-end smartphone or best electric car) is the invention of super-efficient and long-lasting batteries. Systems known as uninterruptible power supplies will also serve the purpose of safeguarding vital constituents of the personal network in case of a power loss.
Endpoint
One of the most important measures of technology advancement is how much easier and simpler it makes life for us. Dream machines of the future, that is, PCs based on cutting-edge technology, will ensure that your refrigerator orders the orange juice when it is about to finish. You will not need to waste time standing in queues at supermarket cash counters—radio frequency identification tags in each of the items will automatically debit the required amount from your account.

Your car service centre will be able to detect car problems remotely using diagnostic software, and rectify these by downloading repair software straight on to your car using the Internet. Perhaps, most of your communication and interaction with appliances will be via voice using speech recognition and, moreover, digital assistants will be available to provide you with useful guidance.

Deep computing, a technology that emphasises on analysing data patterns and extracting valuable information from very large databases, is likely to become quite popular, and will be accessible by even small enterprises. With its origin in IBM chess-playing computer Deep Blue, deep-computing techniques will be used in various sectors such as simulation of new medicines and chemical processes.

Drugs will no longer be designed by mixing chemicals and testing on animals, as scientists will do the efficacy testing on a computer. Personal computers will be able to recognise the current user and visually present customised interfaces. For example, interface for a young child will be different from an interface for a parent.
There are no physical limits to improvements and progress in computer technology. Various aspects such as bandwidth, storage and compute power are likely to evolve, and you can expect to see several manifold improvement. One of the main reasons for this optimism is that the amount of power required in a compute step is not as much as thought earlier.
The quantum of energy needed to execute one compute operation is close to the energy of the atom itself, and it is conceivable to store several bits in an atom. In times to come, personal computing will evolve into intra-personal and intra-cellular beings. There will be a time when, perhaps, each human neuron will be commandeered by a molecular network that grows and repairs itself.
Computers will become networks of polymer filaments growing inside and together with a human being. Probably, elements of these polymer filament based networks will be inserted into embryos in the first month itself of their growth. These will grow to develop into an enormous network inside the brain. Hence, computers will be inside each of us from birth, and thereafter these will unite all living beings into an integrated computing network.
Deepak Halan is currently associate professor at School of Management Sciences, Apeejay Stya University